React2Shell betrifft weiterhin Unternehmen weltweit. Hier sind unsere Beobachtungen und die Maßnahmen, die Unternehmen ergreifen sollten, darunter die sofortige Identifizierung und Behebung von Schwachstellen in Anwendungen.
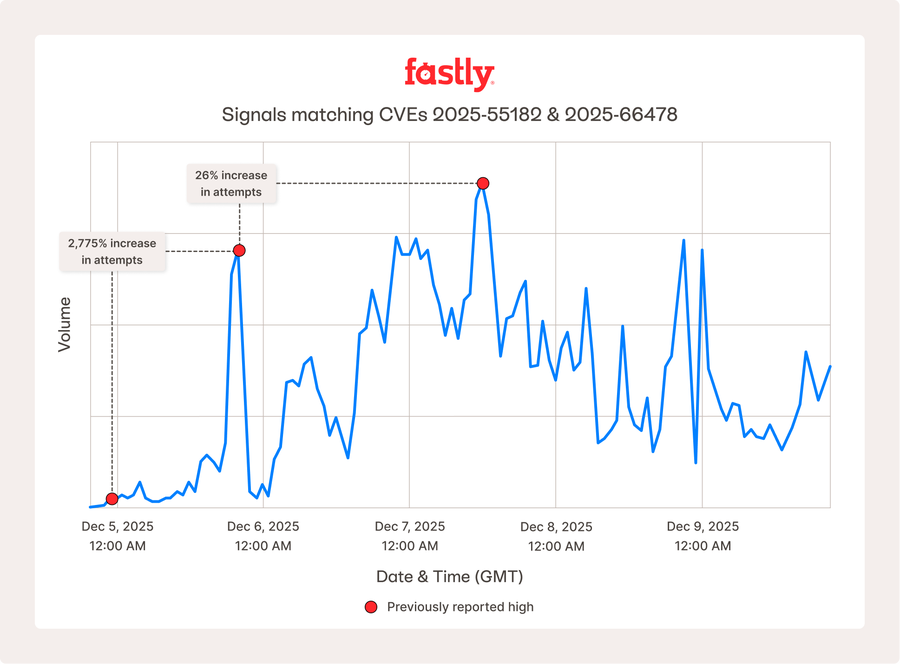
Seit unserem letzten Update am Freitag, dem 5. Dezember, verzeichnete Fastly über das Wochenende hinweg weiterhin ein hohes, anhaltendes Volumen an React2Shell-Aktivitäten in unserem globalen Netzwerk. Um unseren Kunden und der breiteren Community zu helfen, diese prekäre Situation souverän zu meistern, stellen wir zusätzliche Informationen zur Verfügung, die auf den aktuellen Branchen- und geografischen Trends basieren.
Auch jetzt ist die wichtigste Maßnahme, Ihre React- oder Next.js-Anwendungen zu identifizieren und zu aktualisieren, die anfällig für CVE-2025-55182 sind. Die Sicherheitsprodukte von Fastly, einschließlich unserer NGWAF- und Bot-Management-Produkte, können Ihnen Spielraum für Patches verschaffen, sind aber kein Ersatz für Patches. Wenn Fastly Ihnen beim Patching helfen kann, wenden Sie sich bitte an CVE-Alert@fastly.com.
Warum React2Shell für Unternehmen wichtig ist
React2Shell spiegelt ein außergewöhnliches „Patch now“-Szenario wider, da sowohl die Skalierung als auch das Erreichen des angestrebten Ergebnisses für Angreifer einfach sind. Wie ich bereits erwähnt habe, sollten Unternehmen entscheiden, ob sie sich um eine Schwachstelle kümmern sollten, indem sie Folgendes bewerten:
Wie einfach lässt sich der Angriff automatisieren und skalieren?
Wie viele Schritte ist der Angriff vom Zielergebnis des Angreifers entfernt?
Im Fall von React2Shell können Angreifer nun einen der vielen öffentlich verfügbaren Proof of Concepts nutzen, um die Schwachstelle in großem Maßstab auszunutzen – die Untersuchung und die anschließende Ausnutzung lassen sich ohne großen Aufwand automatisieren.
Als Schwachstelle für die Ausführung von Remote-Code vor der Authentifizierung bietet React2Shell Angreifern eine „Ein-Schritt“-Möglichkeit, beliebige Kontrolle über einen anfälligen Anwendungsserver zu erlangen. Wenn Ihr Server anfällig ist, können Angreifer React2Shell instrumentalisieren und sofort eine Vielzahl von Problemen verursachen, von der Exfiltration sensibler Daten über das Entwenden kritischer Authentifizierungsschlüssel und das Modifizieren von Konfigurationsdateien mit eigennütziger Logik bis hin zum Ausführen kostspieliger Kryptominer.
Einfach ausgedrückt: Dies ist eine außergewöhnliche Schwachstelle; Angreifer können React2Shell auf triviale Weise nutzen, um Umsatzströme zu stören, Sicherheitsverletzungen von Kundendaten zu verursachen und die Effizienz Ihrer Betriebsausgaben (OpEx) zu beeinträchtigen. Angesichts der einfachen Verwendung als Waffe und der potenziellen Auswirkungen auf das Geschäft sollten Unternehmen dem Patchen sofort Priorität einräumen.
Mit React2Shell anvisierte Branchen
Fastly beobachtet weiterhin, dass eine Vielzahl von Branchen von React2Shell-Aktivitäten betroffen ist – sowohl bei Sondierungen/Scans als auch bei Ausnutzungsversuchen. Wir glauben, dass derzeit keine Branche mehr unberührt bleibt; Cyberkriminelle scheinen einen Ansatz der „Ökonomie der Skalierung“ zu verfolgen und experimentieren mit breit angelegter Ausnutzung, um ihre ruchlosen Pläne umzusetzen. Zum Beispiel sehen wir, dass einige Angreifer SQL-Injection (SQLi) in den „next-action“-Header einstreuen – und dabei vielfältige Angriffs-Payloads überall verteilen, um zu sehen, was hängen bleibt.
Fastly hat die Aktivitäten von React2Shell dokumentiert, die sich auf Branchen auswirken, darunter unter anderem die in der folgenden Infografik aufgeführten.

Wir sehen auch eine gewisse Korrelation zwischen den am häufigsten ins Visier genommenen Branchen und denjenigen, die am ehesten sensible Finanzdaten – oder anderweitig lukrative, vertrauliche Daten – in ihren Anwendungen enthalten.
Organisationen, die als Plattformen dienen, gehören laut unseren Daten zu den am häufigsten angegriffenen – und diese Plattformen sind oft vertikal spezifisch. Unsere Hypothese ist, dass Angreifer Plattformen als ein besonders lukratives Ziel betrachten, da eine beliebige Kontrolle über die Anwendungsserver von Plattformen Folgendes erleichtern kann:
Das Stehlen von Schlüsseln, die den Zugang zu den Systemen anderer Organisationen erleichtern (da Plattformen in vielen Fällen Zehntausende von Organisationen bedienen)
Exfiltration der Kundendaten der Plattformen (da Anwendungsserver die Schnittstelle darstellen, durch die Kundendaten zur und von der Datenbank fließen)
Betrieb von Kryptominern (wie XMRig), da viele Plattformen aufgrund ihres Maßstabs „leistungskräftigere“ Server kaufen
Ändern von Konfigurationsdateien, um von Angreifern kontrollierte Services auf die Zulassungsliste zu setzen und den Zugriff aufrechtzuerhalten
Und jede andere Aktion, die der Angreifer monetarisieren oder anderweitig nutzen kann, um seine Mission zu erfüllen, da er nun die vollständige Kontrolle über den Anwendungsserver hat
Um es klarzustellen: Diese Maßnahmen gelten gleichermaßen für andere Branchen und Arten von Organisationen, wobei die Auswirkungen auf die Kunden der Organisation in unterschiedlichem Ausmaß n-ter Ordnung sind.
Geografische Ziele von React2Shell
Fastly verzeichnet außerdem React2Shell-Aktivitäten in allen Teilregionen unseres globalen Netzwerks.
In verschiedenen Teilregionen scheinen unterschiedliche Sondierungs- und Angriffsmuster aufzutreten; beispielsweise kommt es in einigen Regionen häufiger zu WAF-Umgehungsversuchen als in anderen. Unsere Hypothese ist, dass Angreifer möglicherweise davon ausgehen, dass einige Sub-Regionen weniger wahrscheinlich NGWAF oder andere proaktive Schutzmechanismen vor ihren Anwendungsservern einsetzen, während Angreifer beispielsweise anscheinend davon ausgehen, dass die meisten Organisationen mit Sitz in den Vereinigten Staaten über eine WAF verfügen.
Wir sehen auch, dass dieselben Angreifer anscheinend mehrere geografische Regionen ins Visier nehmen. Dies bestätigt unsere Hypothese, dass Cyberkriminelle React2Shell in großem Maßstab nutzen und nach allen Organisationen suchen, die möglicherweise verwundbare Anwendungsserver haben, unabhängig von deren Standort.
Derzeit scheinen Angreifer WAF-Umgehungen nicht in gleichem Maße zu versuchen wie allgemeinere Exploit-Versuche. In einigen Teilregionen machen Umgehungsaktivitäten nur einen einstelligen Prozentsatz aller Angriffsaktivitäten aus.
Unsere Hypothese lautet, dass Angreifer möglicherweise den ROI ihrer WAF-Umgehungen erhalten möchten und daher nur dann solche Versuche unternehmen, wenn sie bestimmte Organisationen ins Visier nehmen, um die Verteidiger nicht zu alarmieren und damit die Umgehungen unbrauchbar zu machen. Fastly erkennt also unterschiedliche JA4-Signaturen bei Angreifern, die den groß angelegten Ansatz des „Goldwaschens“ verfolgen, im Vergleich zu Angreifern, die WAF-Umgehungen ausnutzen.
Natürlich erkennt Fastly diese Umgehungsversuche, um diese Informationen zu generieren; wir vermuten, dass unsere Abwehr auch zu dem steilen Rückgang der Umgehungsversuche geführt hat, den wir beobachten konnten, nachdem die Angreifer zum ersten Mal versucht hatten, sie zu nutzen.
Fazit
Unsere Empfehlung bleibt konsistent: Identifizieren und aktualisieren Sie Ihre React- und Next.js-Anwendungen so schnell wie möglich und wenden Sie proaktive Schutzmaßnahmen an, um Angriffsversuche zu verhindern. Die Sicherheitsproduktpalette von Fastly, einschließlich unserer NGWAF- und Bot-Management-Produkte, kann Ihnen Zeit zum Patchen verschaffen.
Fastly beobachtet weiterhin, wie Angreifer ihre Sonden, Scans und Exploits weiterentwickeln, während die Marktdynamik schwankt. Jedes Unternehmen mit anfälligen Anwendungen – unabhängig von der Branche oder Region – sollte davon ausgehen, dass Angreifer sie bereits zumindest testen und wahrscheinlich versuchen, sie zu instrumentalisieren. Nach dem Patchen sollten Sie auf jeden Fall nach weiteren Updates Ausschau halten, da diese Arten von Angriffen mit hohem Return on Investment dazu neigen, weitere Varianten hervorzubringen und Schwachstellenforscher dazu zu inspirieren, weitere ausnutzbare Fehler in ähnlichen Bereichen zu finden.
Wie immer sollte unser Ziel, und das Ziel aller Organisationen, darin bestehen, die Kosten von Angriffen zu erhöhen, um den Return on Investment von Cyberkriminellen und Nationalstaaten gleichermaßen zu schmälern. Wenden Sie sich an Fastly unter CVE-Alert@fastly.com, wenn wir Ihnen bei der Navigation durch den Prozess des Patchens oder Schutzes Ihrer Anwendungen helfen können.

