Fastly の2025年5月の独占 DDoS 脅威レポートによると、5月には毎分2件近くの新たな攻撃が開始されたことが判明した。
Fastly のインスタント・グローバル・ネットワークでは、数兆件に上るレイヤー3およびレイヤー4の DDoS 攻撃の試みを阻止してきました。しかし、高度な新しいレイヤー7攻撃は検出が難しく、潜在的にはるかに危険です。インターネットに接続されたアプリケーションや API のパフォーマンスと可用性に対するこの重大な脅威は、ユーザーと組織を危険にさらします。Fastly では、1日あたり1.8兆件のリクエストを処理する、427テラビット/秒*の容量を持つグローバルエッジネットワークと、Fastly DDoS Protection から取得したテレメトリに基づき、アプリケーションに対するグローバルな DDoS 攻撃の状況に関する独自のインサイトを提供しています。DDoS に関するまさに唯一無二の月次レポートです。アプリケーションを狙った最新の DDoS 攻撃のトレンドに関する匿名データ、インサイト、実用的なガイダンスを共有し、セキュリティへの取り組み強化をサポートします。
レポートに見られたプロダクト強化の影響
Fastly は10年以上にわたり、自社プラットフォームやその他のソリューションを利用してこれらの脅威を軽減し、大規模な分散型 DDoS 攻撃と戦ってきました。そして、お客様に適応型かつ自動的な軽減策を提供するために、2024年10月に Fastly DDoS Protection をリリースしました。以来、アプリケーションへの分散型 DDoS 攻撃対策として最高のソリューションとするべく、懸命に取り組み続けています。このソリューションの Adaptive Threat Engine が攻撃に対抗する上でどれほど強力であるかを詳しく説明してきましたが、私たちはその基盤を強化し、検知能力を向上させるために引き続き努力しています。
この機能強化により、検出時間がさらに短縮され、DDoS 攻撃 (特に短時間の小規模な攻撃) に対するソリューションの可視性が向上しました。私たちは継続的にコアとなる検出機能と緩和機能の改善に努めており、これが4月と5月に攻撃数が一貫して増加した一因であると考えられます。Fastly では、お客様にさらに優れたプロダクトを提供できるよう今後もプロダクトを改良し続けますが、このような機能強化の影響がレポートに反映されることが予想されます。免責事項についてご理解いただいたところで、早速結果を見てみましょう。
主な調査結果
Fastly DDoS Protection は5月に平均して1分あたりほぼ2件の攻撃を観測しました。
5月の攻撃の最高割合は、木曜日と金曜日の 14:00~20:00 (UTC) の間に発生しました。
国が自動生成されたルールの一部として使用される場合、最も一般的なのはアメリカ合衆国 (41%) です。
DDoS トラフィックの傾向
5月のアプリケーション DDoS 攻撃は、月全体にわたって分散していましたが、2025年5月6日に大きなピークがあり、その日の累積攻撃数は月平均の1.8倍に達しました。5月6日の攻撃はメディア&エンターテインメント企業を中心に行われ、その日の総攻撃量の93%を占めていましたが、攻撃を受けた企業は業界内で類似した業種に属していないため、組織的なキャンペーンの一部であるようには見えません。

DDoS 攻撃の量は2025年の各月で増加し、5月には前月比で4月より1%未満の減少にとどまりました。今後数か月、この傾向を引き続き監視していきます。こちらにもっとあります!

Fastly DDoS Protection が5月に検出した最大の攻撃は1時間以上続き、1秒あたりのリクエスト数 (RPS) は100万を超えました。前回のブログで説明した2億5000万RPSの攻撃ほど大規模ではありませんが、攻撃者が持つ持続的な攻撃能力を垣間見ることができます。
攻撃トレンド
これらのイベントは、Fastly DDoS Protection の最新アップデートの一環として発生したものです。これには、イベントとイベントの詳細という2つの主要な機能が付属しています。各イベントが個別の攻撃であり、イベントの詳細によって、お客様は、どのように攻撃が軽減されたかを深く掘り下げることができるとお考えください。5月、Fastly DDoS Protection は累計77,459件のDDoS攻撃を観測し、これをイベントとして分類しました。それらを均等に分配すると、5月の1分ごとにほぼ2つのイベントが発生していたことになります!
以前の版のレポートでは、時間と曜日別の攻撃量の分布を示すヒートマップを作成しました。今月はそのヒートマップを再作成することにしましたが、今回は時間と曜日ごとにイベントを通してそれを見てみることにしました。

イベントの観点から攻撃を観察すると、攻撃は週を通して全時間に発生していますが、最も多くの攻撃が発生するのは木曜日と金曜日の 14:00~20:00 (UTC) の間であることが分かります。この時間帯が西洋諸国のほとんどで営業時間中であることを考慮すると、これは特に興味深いです。これを、攻撃の大半が米国を標的にしたルールを自動的に作成できたというインサイトと組み合わせると、興味深い結論に達します。通常、西欧諸国では営業時間外や週末に攻撃が行われることが確認されていますが、5月の攻撃は、これらの組織が地域内で SOC メンバーが監視している間に発生しました。各顧客からの追加情報がなければ、5月が確立されたトレンドから逸脱した理由を正確に知ることは難しいですが、考えられる説明は次のとおりです。
身代金要求の試み: このレポートで観察されたすべての攻撃は、ブロックモードの Fastly DDoS Protection で軽減可能ですが、すべてのお客様が切り替えたわけではありません。このような露骨な攻撃は、SOC アナリストの注意を引き、支配を主張するために行われた可能性があります。
地政学的変化へのレスポンス: 米国、ヨーロッパ、アジア太平洋地域の一部での政治的決定の合間に、攻撃者は刺激を受けた投稿やニュースに反応して、Fastly のメディア & エンターテインメントのお客様に攻撃を仕掛けた可能性があります。
これらのレポートでは攻撃量と攻撃件数を常に比較してきましたが、今後はイベントを使用して攻撃件数を表し、Fastly のお客様が観測している攻撃件数をさらに正確に測定します。幸いなことに、以前の読者にとって、このデータは業界や企業の規模に関係なく、過去数か月間に観察されたものと非常に似ています。
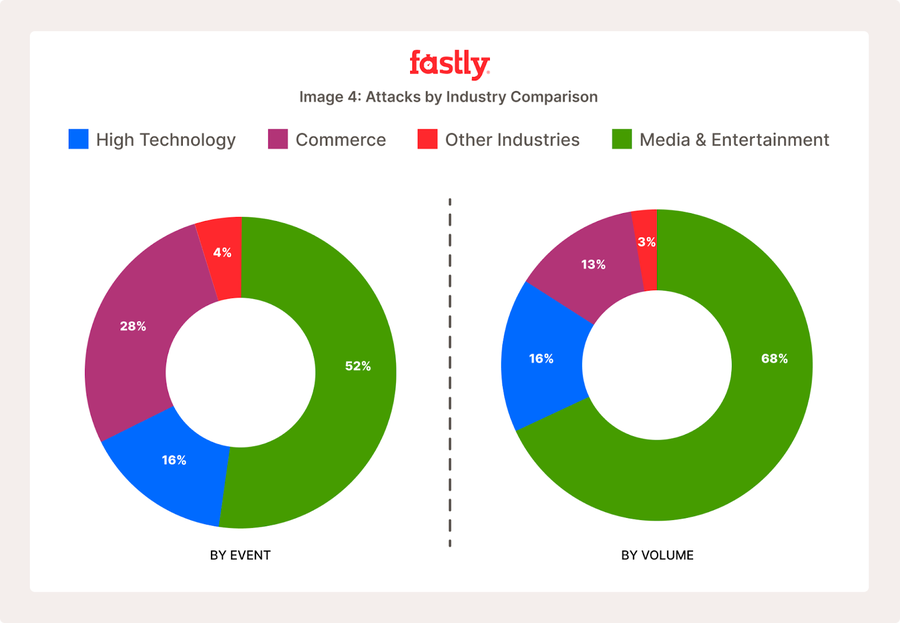
攻撃の標的となる業界を観察すると、メディア & エンターテインメントが引き続き攻撃者の主な標的となっています。5月の攻撃が主に西洋の営業時間中に発生した理由についての私たちの仮説と同様に、ハクティビストや動機のある攻撃者が、自分たちの見解に反する内容を表示する組織に対して攻撃を仕掛ける動機が高まった可能性があります。通常、メディア & エンターテイメントの攻撃件数の割合は低いですが、すべてのイベントの半分以上を占めていることから、この業界への攻撃は、たとえば4月の攻撃と比較すると比較的小規模ですが、より頻繁に行われていることを示しています。
企業規模別に攻撃を分析すると、5月の攻撃の大部分 (66%) がエンタープライズ規模の組織を標的にしていることが明らかになりました。これらのレポートを初めてご覧になる方のために、企業規模の内訳を次のように説明します。
エンタープライズ: 10億ドルを超える
商業: 1億ドル~10億ドル
中小企業 (SMB): 1億ドル未満

対照的に、イベント数は SMB 組織に大きく結びついています。エンタープライズへの攻撃量の分布は前月に比べて大幅に増加しましたが、この傾向は、エンタープライズ組織がより多くの攻撃量を受ける一方で、中小企業はより多くの個別攻撃を受けるという観察結果と一致しています。
軽減トレンド
イベントの詳細の一環として、Fastly DDoS Protection ではイベントに関連するすべてのルールを表示します。これらのルールから、攻撃の属性の傾向を観察し、チームがセキュリティポリシーを策定するのに役立ちます。
5月にイベントを軽減するには、平均して3.2個のルールが必要でした。先ほど触れたように、ルールの67%には、攻撃者の国が自動生成されたルールの一部として含まれていました。ルールに含まれる上位5か国は以下の通りです。
米国 (41%)
ドイツ (9%)
オランダ (5%)
インドネシア (5%)
シンガポール (5%)

4月のレポートでは、攻撃の一部がアメリカのサイバー攻撃者によって行われている可能性が高いと指摘しましたが、サーバーレスインスタンスの起動は非常に容易でアクセスしやすいことがわかりました。攻撃者は、わずかな労力で、選択した自律システム (AS) を活用し、実際の場所に関係なく、世界中のほぼどこからでも攻撃を発信することができます。これが、ルールにアメリカ合衆国が頻繁に登場する理由の一つです。それとも…アメリカは攻撃者で溢れているだけなのか、時が経てば分かるでしょう。
Fastly DDoS Protection ルールの一部として使用されるもう1つの属性はIPアドレスです。場合によっては、攻撃が単一の IP に絞り込まれることがあり、5月にはこれが35%の確率で発生しました。

これを4月の調査結果 (31%) と比較すると、分布にわずかな増加が見られます。このインサイトから、アプリケーション DDoS 攻撃の状況は、攻撃方法の点では比較的ゆっくりと変化していると推測できます。個々の組織レベルで攻撃を阻止するのは複雑であり、何らかの形で自動化された介入が必要になる可能性があります。しかし、Fastly の視点から見ると、毎月の攻撃の大部分には共通して繰り返されるテーマがあることがわかります。年間を通じて攻撃の量は増加していますが、マクロ的な視点では攻撃自体はほとんど変わっていません。これは、攻撃者が現在のアプローチで成功を収めているためかもしれません。
Fastly DDoS Protection などのツールにアクセスできるお客様は、このような攻撃を心配する必要はありません。しかし、変化の速度が遅いことは、世界中の多くの組織がこのレベルの保護にアクセスできないか、アクセスできても不十分であることを示唆している可能性があります。そうでなければ、攻撃を仕掛ける意味がないでしょう。
実用的なアドバイス
これらのデータの重要ポイント
このレポートは1か月分のデータのみを表しており、包括的に状況を把握するには、オブザーバビリティツールが提供するファーストパーティのインサイトや長期的な調査と併せてこのデータを活用する必要があることに留意してください。しかしながら、このデータだけでも、既存のセキュリティ対策に組み込むことができる重要な学びがあります。
5月の攻撃量は4月よりわずかに少なかったものの、それでも第1四半期の他のどの月よりもはるかに多い結果になりました。コンテンツをキャッシュすることでオリジンサーバーの負荷をいくらか軽減できますが、正当なトラフィックと攻撃トラフィックのさまざまなパターンに適応できる専用の DDoS ソリューションの実装をご検討ください。
セキュリティ担当者と組織のリーダーは、脅威の状況を理解し、業界に関連する特定のリスクを評価した上で、それに基づいて防御戦略を実施する必要があります。例えば、ペットの里親あっせんに注力している企業は、ハクティビストから国家レベルの攻撃者までさまざまな脅威に直面する可能性のあるメディア組織に比べると、攻撃対象としての魅力は低いと考えられます。
攻撃量は週を通して比較的安定していましたが、木曜日と金曜日の 14:00~20:00 (UTC) にピークを迎えました。EMEA または APAC で活動する組織にとって、24時間365日体制のセキュリティ・オペレーション・センター (SOC) の重要性が浮き彫りになりました。
ビジネスに支障をもたらす分散型攻撃を自動的に軽減
いつものようにお伝えしておきますが、Fastly DDoS Protection などのソリューションは、このレポートで報告されているタイプの攻撃を自動的に阻止し、その有効性を迅速に検証するために必要なインサイトを提供します。Fastly DDoS Protection では、Gartner Peer Insights で同業者から4.7/5つ星の評価を受けており、ネットワークの大規模な帯域幅と適応技術を活用して、必要な設定なしで Web サイトの高速性と可用性を確保します。今すぐ Fastly のアダプティブテクノロジーを活用して、最大500,000件のリクエストを無料で取得しましょう。または、詳細について Fastly のチームにお問い合わせください。
* 2025年3月31日現在
** 2023年7月31日時点


