Fastly Adaptive Threat Engine
Fastly DDoS Protection leverages our Adaptive Threat Engine to automatically detect, identify, and mitigate application DDoS attacks.
On this page
DDoS attacks can quickly overwhelm applications and APIs, resulting in performance issues, inflated Operational costs, or downtime. The Adaptive Threat Engine powering Fastly DDoS Protection automatically detects, identifies, and mitigates DDoS attacks before they can impact your customers and bottom line. The engine is built on three core principles that enable it to accurately mitigate attacks in seconds:
Everything starts with rapid, accurate detection of malicious traffic
Avoiding false positives is priority, so mitigations are safe to run
Defense tactics should be deceptive, minimizing information available to attackers
Rapid, accurate detection of malicious traffic
Rapid detection is core to mitigating the impact of attacks. Most quickly scale from zero requests per second (RPS) to millions or hundreds of millions of RPS and often finish less than a minute later. When looking at the attacks Fastly saw from over 90 days of data, the attack is often over by the time a human can be made aware of an attack and equipped to respond. (Image 1):
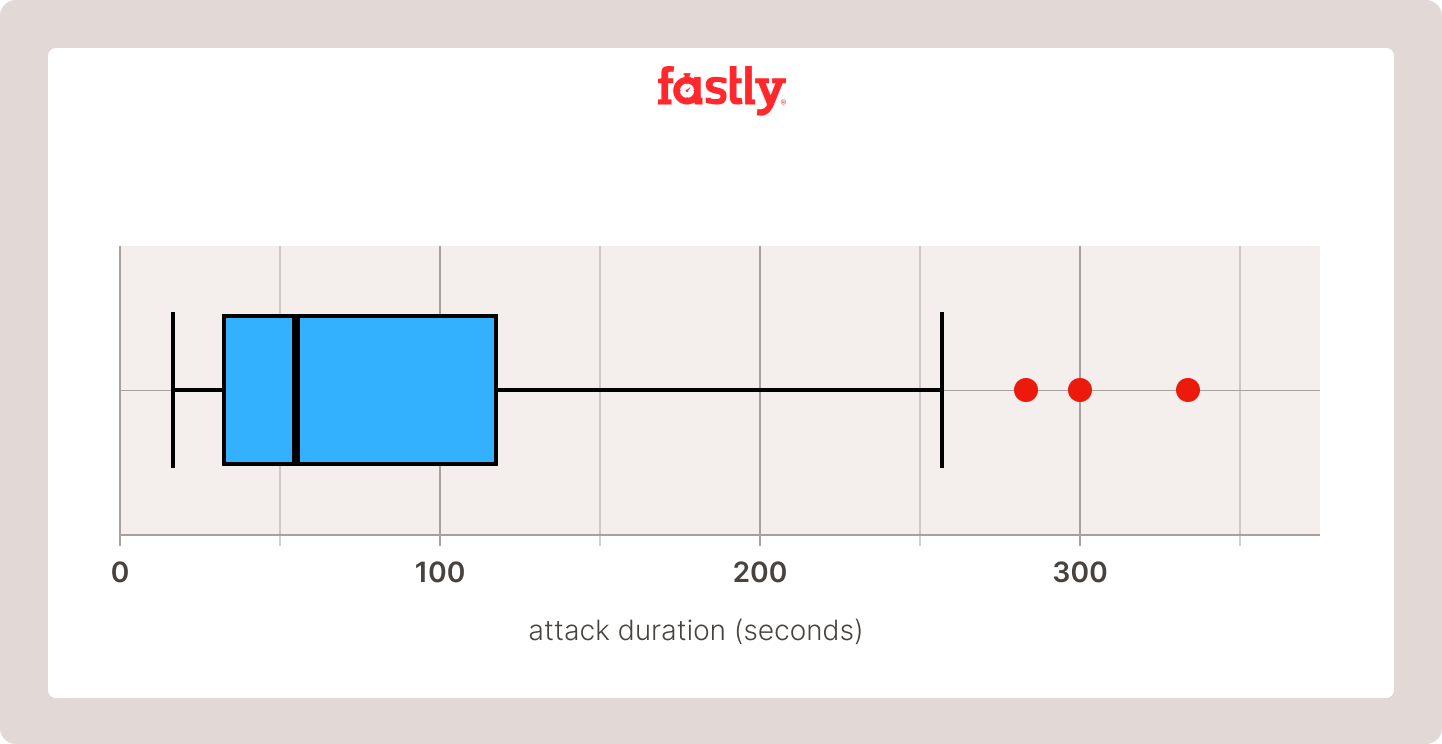
Image 1: Observed attack duration in seconds*
90% of the attacks have a total duration of 150 seconds or less
50% of the attacks are under 52 seconds
To mitigate as fast as possible, Fastly DDoS Protection leverages the Adaptive Threat Engine's processing and decision-making across the global edge rather than running through a centralized function that has less capacity and inevitably serves as a bottleneck. Our software-defined network removes dependencies on specialized hardware and other components like routers. It gives our Adaptive Threat Engine the power and flexibility to rapidly process, analyze, diagnose, and respond effectively without impacting legitimate traffic.
Accurate Detection
Identifying and distinguishing attacks from organic traffic can be challenging because advanced attacks often blend with legitimate traffic. Assuming teams can identify the attack manually, this also means that it costs more for your defense team to mitigate it (time, resources, computation, business impact, etc). The Adaptive Threat Engine takes a two-step approach to accurately detecting attacks. It creates custom, continuously-updated baselines for total traffic throughput AND over 10 behavioral and client-based traits for every service it operates on.
By considering both the nature of the traffic spike and its traits when detecting whether your service is experiencing an influx of legitimate traffic or an attack, the engine can minimize false positives. This approach enables legitimate traffic to quickly rise due to a sale, busy season, viral moment, etc., but if the attributes remain normally distributed, no action is taken.
When both traffic rate and attributes significantly deviate from their baselines, the Adaptive Threat Engine extracts accurate attacker identities from a comprehensive list of traits in Layer 3 and Layer 4 headers, TLS information, Layer 7 details, and more. This includes characteristics like IP address, user agent, TLS properties, geographic location, and more. It extracts metadata from inbound requests and computes elements that match the attack. This process is the most accurate and safe way to detect attackers for mitigation because nearly every attack has unique characteristics. To maximize accuracy, the Adaptive Threat Enginehe repeats this process for every attack and doesn’t rely on long-term static rules like other solutions that can be prone to false positives.
The Adaptive Threat Engine is also built on a modular system that enables us to rapidly enhance detection and mitigation capabilities as new classes of attacks are discovered without needing to develop an entirely new mechanism to respond. When new attacks like the Rapid Reset attack come along, Fastly implements new functions in detection and response modules, which keep response times incredibly short, even for novel attacks.
Best of all, you never need to worry when it’s happening because it rapidly and accurately detects DDoS attacks for mitigation automatically.
Safe mitigation
Every automated system has a risk of generating false positives and blocking legitimate traffic. Automated systems alone or in combination with human error have a long history of creating outages, but if policies become too lenient actual attacks are let through.
Building on rapid detection and accurate signature extraction, the Adaptive Threat Engine implements safe mitigations without impacting legitimate traffic. Its mitigations are always on and are considered safe at all times without consequence because they’ve gone through in-depth validation and code review processes. For example, there are built-in controls to prevent rules from being made on single attributes that are prone to false positives, like country code. Additionally, the engine can’t be overwhelmed by multiple synchronized attacks and is also capable of mitigating multiple attacks simultaneously, ensuring your services remain performant and available regardless of the adversary. Lastly, the Adaptive Threat Engine maintains multiple continuously updated samples of your normal traffic and compares any intended rules against them. When too much traffic overlaps with an intended rule, it's never published.
Deceptive tactics
Information is power when it comes to DDoS attacks. When attackers learn something about a network or gain insight from their previous attempts, it informs how they execute their next attack. It’s a cat-and-mouse game of constant evolution, and by withholding information from the attackers, you are making them work harder to figure out if they need to change tactics or how they should adapt. When most platforms detect an attack they act swiftly to close the connection on the attacker or deny access to their platform in another way. This signals to the attacker that they’ve been discovered, and also that if they try the same approach again it is likely to be more easily identified and blocked. the Adaptive Threat Engine aims to intentionally minimize the amount of information (of any form) that is sent back to the attackers.
The Adaptive Threat Engine in action
Here’s a simplified example of the engine detecting, identifying, and mitigating a DDoS attack against one of our customers. The Adaptive Threat Engine monitors traffic at all times for anomalous spikes in traffic patterns and their traits(Image 2).

Image 2: Detection of sample attack
When an attack is detected, the Adaptive Threat Engine works in milliseconds to test individual attributes until it finds one that best aligns with the attack curve (Image 3).
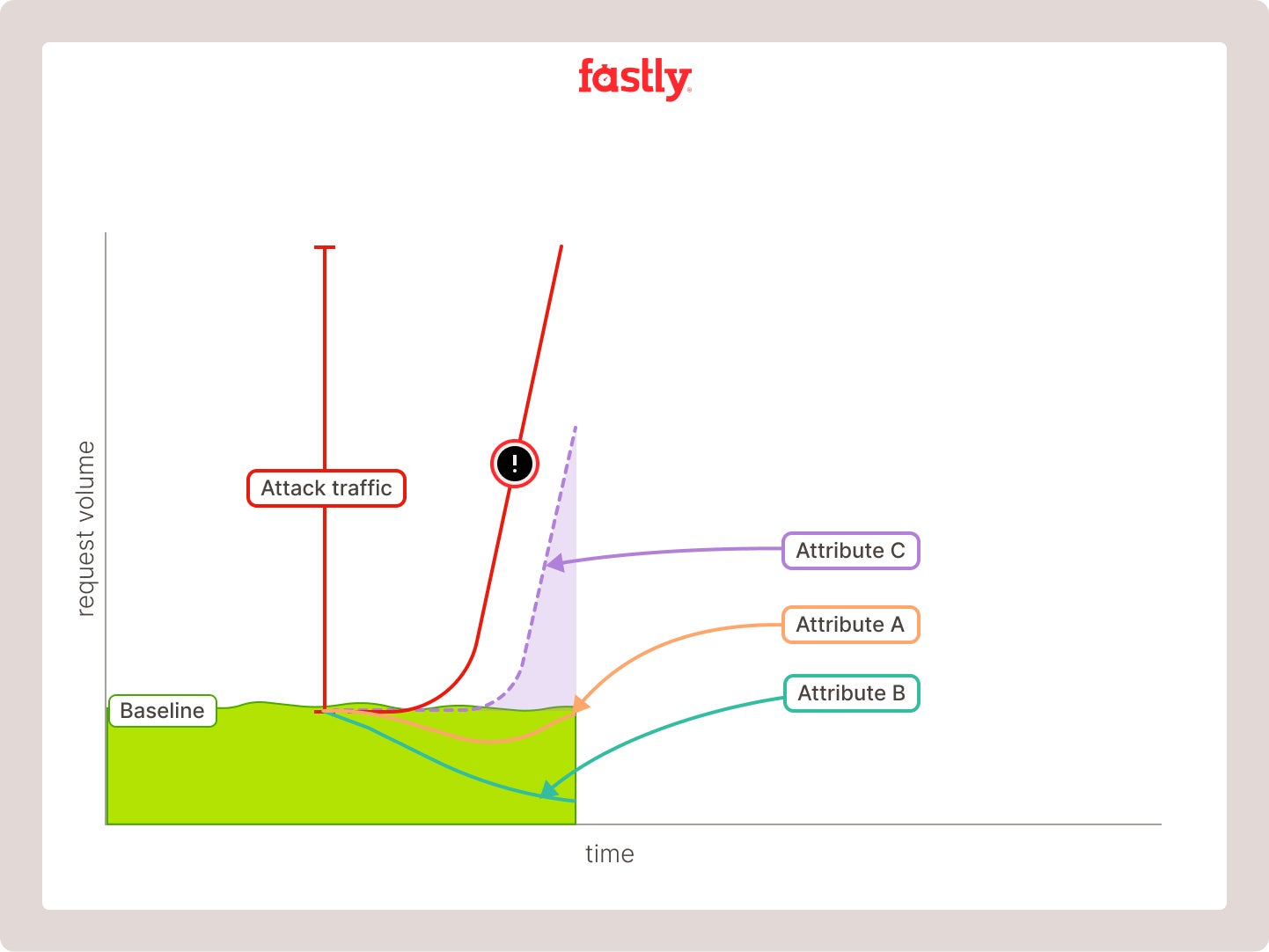
Image 3: Testing individual attributes
Once the engine finds an initial best-match attribute, it quickly repeats the process, combining additional traits to build an equation that gets closer to representing the surplus of attack traffic. With each additional trait added to the equation, the degrees of freedom required to further improve the model decrease. This process continues until the Adaptive Threat Engine creates a unique equation that matches the surplus of attack traffic, and it confidently blocks the attacker's unique identity (Image 4).
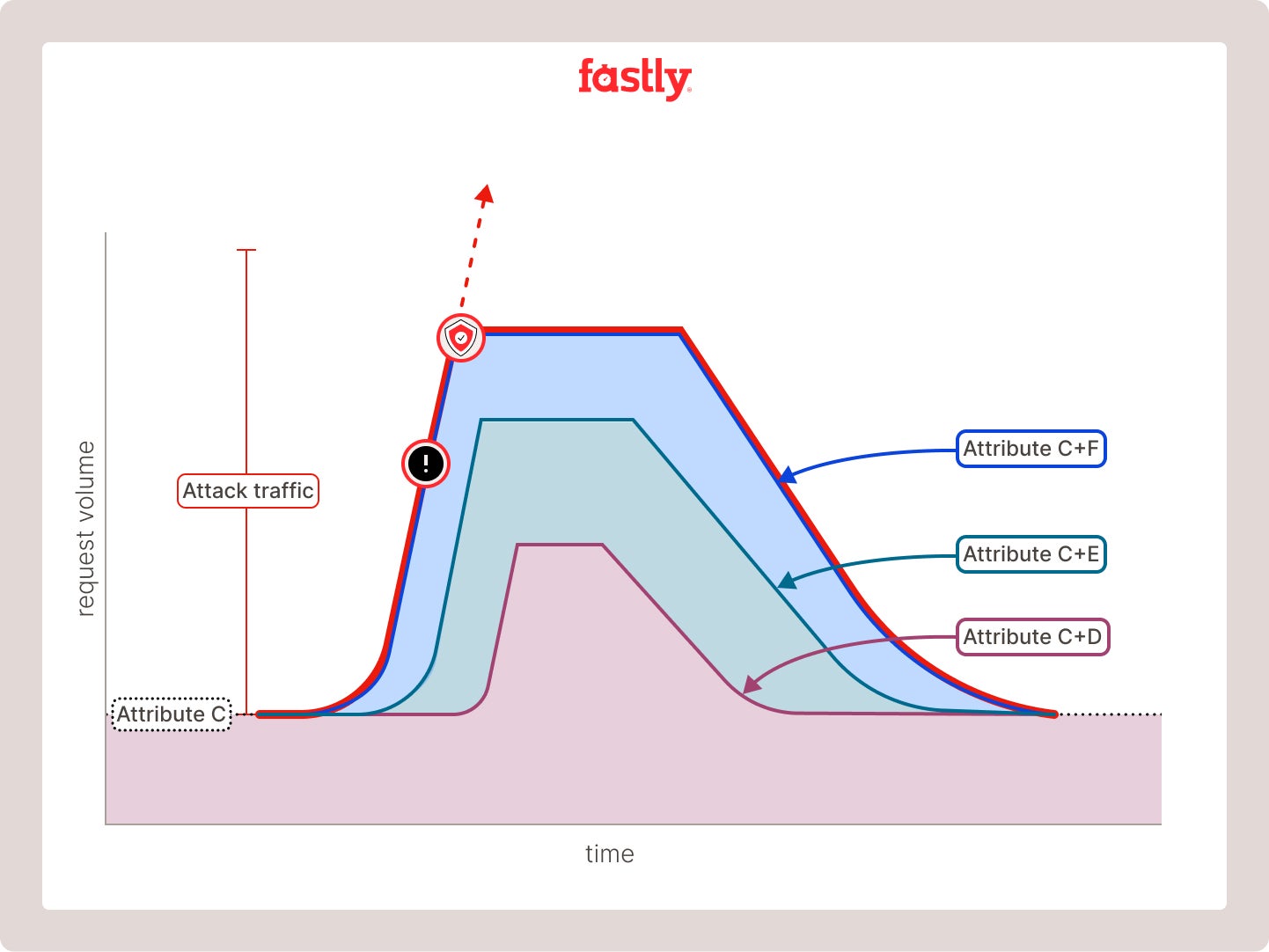
Image 4: Testing sets of attributes
This might sound like a computationally intensive process, but detection, identification, and mitigation occur in seconds because of the power and speed of Fastly’s global edge. While this example involved a single attack, it can also simultaneously defend against multiple targeted attacks from different malicious actors.
Exploring the Adaptive Threat Engine’s rules
Fastly DDoS Protection gives visibility to every rule the engine automatically creates to mitigate an attack; each contains a summary of the traits it is blocking against and the traffic impacted (Image 5).

Image 5: Example of the Adaptive Threat Engine's Rules
With this information, organizations can quickly validate the efficacy of the rules. Take the example above – the rule was built in seconds to mitigate an attack on a major retail organization. You can feel confident in the efficacy of the mitigation because:
A single IP generated a spike in both the volume and diversity of requests, causing Fastly DDoS Protection to flag the behavior as a DDoS attack
The intended rule didn't overlap with any traffic samples
Upon examination, the user agent is a known enumeration tool used by cyber attackers
Upon examination, the path they were targeting doesn’t exist for this customer
Upon examination, the entirety of surplus attack traffic came from a single country that the organization doesn’t typically receive end users from
Every rule also features an editable status, allowing teams to tailor their defense. Should this rule have been deemed permissible based on the business context only your operators have, you can easily adjust the behavior to fit your needs. Other instances where this flexibility is helpful include when someone has just purchased the product and is temporarily in logging mode, can move individual rules into blocking, or those who must allow volumetric bursts of traffic for testing purposes.
Where other competitive solutions are popularizing their ability to block in milliseconds using static rules that may be prone to error over time (especially with the rise of AI-usage by attackers), Fastly DDoS Protection custom-crafts every rule with this level of tailored accuracy, visibility, and configurability so you can rest easy knowing you’re protected.
Automatically mitigate attacks with Fastly DDoS Protection
As the sophistication and rate of DDoS attacks continue to rise, complex or manual solutions are rendered ineffective. The Adaptive Threat Engine in Fastly DDoS Protection accurately detects, identifies, and mitigates DDoS attacks targeting your Apps and APIs. In seconds, it mitigates attacks without requiring any tuning, ensuring your team doesn�’t spend resources on effective security and that end users don’t experience the performance and availability impacts of attacks. If you'd like to learn more about how Fastly DDoS Protection can help you automatically mitigate the impact of application DDoS attacks, contact us.
**Attack duration data was collected by looking at the ingress requests to Fastly network from 2023-07-01 to 2023-10-12. The onset of attack is registered when a 30% increase from anticipated baseline is detected, and it ends when traffic is back to expected levels. We have excluded known organic traffic spikes and load testing from this dataset.