Actualización del 11 de diciembre:
Desde la publicación de este blog, se ha descubierto que la corrección de la CVE-2025-55184 (descrita a continuación) en React Server Components era incompleta y no evita un ataque de denegación de servicio en un caso concreto. Las versiones 19.0.2, 19.1.3 y 19.2.2 de React Server Components están afectadas porque permiten la deserialización insegura de cargas útiles de peticiones HTTP a puntos finales de React Server Function. Esta vulnerabilidad adicional se recoge en CVE-2025-67779 y las últimas versiones de React puedes encontrarlas aquí.
Tras las graves vulnerabilidades CVE de React2Shell detectadas la semana pasada, se acaban de anunciar dos nuevas vulnerabilidades CVE que aprovechan componentes similares de Next.js y React. Las últimas noticias elevan el nivel de alerta, ya que las organizaciones se apresuran a evaluar el impacto y refuerzan la necesidad de identificar la exposición y aplicar parches a estos marcos subyacentes.
¿Se ven afectados los clientes de Fastly?
En primer lugar, si eres cliente de Fastly, probablemente estés aquí para saber si el uso de los productos Fastly te expone a estas vulnerabilidades. Nuestra evaluación inicial sigue siendo válida a día de hoy: la plataforma y las aplicaciones de Fastly no son vulnerables en este momento.
Sin embargo, ten en cuenta que, aunque Fastly no se ve afectado, tu organización debe evaluar la exposición interna de forma independiente.
¿Qué es React2Shell y cuáles son los últimos CVEs relacionados con él?
Si acabas de ponerte al día con todo lo relacionado con React2Shell, tenemos un artículo en el blog que aborda todas las cuestiones que necesitas saber.
Un breve resumen: el 3 de diciembre se anunciaron dos vulnerabilidades y exposiciones comunes críticas (CVE-2025-55182 y CVE-2025-66478) que afectan a versiones más recientes de componentes de Next.js y React. Estas CVE (ahora denominadas conjuntamente React2Shell) ofrecen a los atacantes la posibilidad de ejecutar código remoto (RCE) sin necesidad de autenticación previa, lo que supone una auténtica mina de oro de datos confidenciales, claves de autorización críticas y mucho más si se aprovechan. Los atacantes pueden actuar a gran escala.
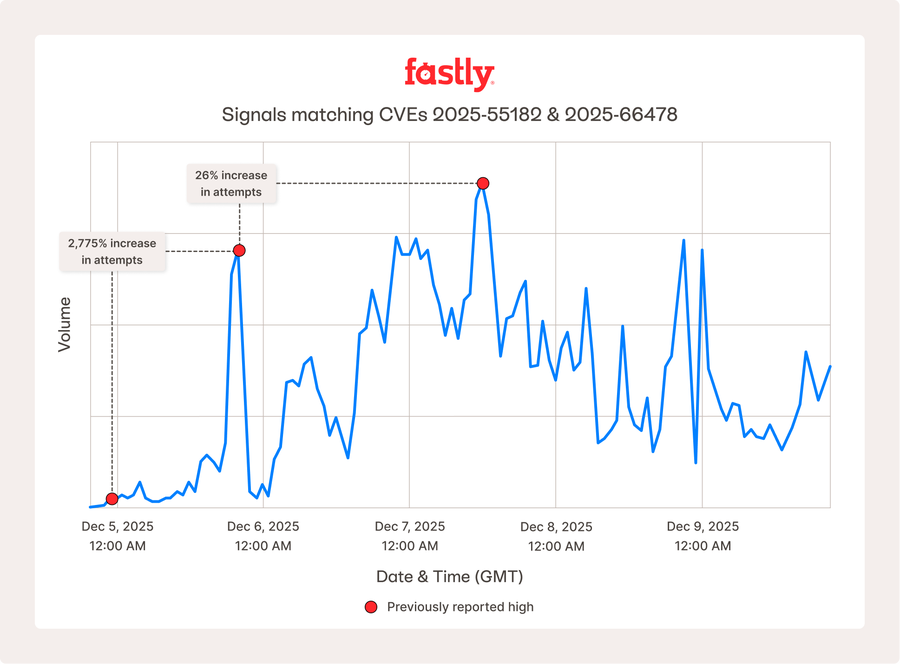
Desde el anuncio de React2Shell, Fastly y la comunidad de seguridad en general han estado trabajando codo con codo para crear parches virtuales, compartir datos y reafirmar al mundo que las organizaciones deben identificar y actualizar sus aplicaciones React y Next.js lo antes posible y aplicar protecciones proactivas para adelantarse a los intentos de ataque.
¿Y qué ha cambiado?
El 11 de diciembre se anunciaron dos nuevas CVE: CVE-2025-55183 y CVE-2025-55184. Estas vulnerabilidades aprovechan componentes similares de Next.js y React Server, pero con fines diferentes: exposición del código fuente de la función (una fuga de información) y denegación de servicio (DoS), en lugar de ejecución remota de código.
Es posible que estas nuevas CVE no sean tan graves como las CVE de React2Shell mencionadas anteriormente; sin embargo, ahora que estas vulnerabilidades se han hecho públicas, los atacantes que ya están investigando las CVE anteriores pueden intentar abusar de estas últimas con la misma facilidad.
¿Qué es la CVE-2025-55183?
Los atacantes pueden aprovechar la CVE-2025-55183 para revelar el código fuente de una React Server Function (RSF), pero no el código fuente de toda la aplicación. Por lo tanto, es probable que esta CVE no sea un problema de gran impacto a menos que:
Usas React Server Components.
Tienes información sensible o propietaria contenida en el código fuente de React Server Function (RSF).
Según nuestro análisis, los atacantes podrían utilizar principalmente esta CVE para realizar reconocimientos, pero necesitarían otras CVE (y los exploits necesarios) para acceder a niveles más profundos o obtener un control arbitrario sobre la aplicación (como se puede lograr con React2Shell).
En cualquier caso, recomendamos encarecidamente no codificar secretos en ninguna parte de tu aplicación, incluidas las RSF. Si utilizas RSF, realiza una auditoría inmediata para asegurarte de que no hay datos confidenciales o de propiedad exclusiva en el código fuente de tus funciones.
¿Qué es la CVE-2025-55184?
Esta CVE facilita un ataque DoS en el que un atacante puede forzar a un servidor de aplicaciones vulnerable a entrar en un bucle infinito mediante la creación de una solicitud específica. Si no dispones de escalado automático o reinicio automático, un atacante podría enviar un patrón específico de solicitudes para forzar a tu servidor de aplicaciones a entrar en un bucle infinito, lo que consumiría CPU y lo mantendría inactivo hasta que se recuperara la aplicación.
Además de actualizar tu aplicación a la versión parcheada, las prácticas de infraestructura modernas también pueden aumentar la resistencia de tus aplicaciones al impacto de CVE-2025-55184. Cualquier configuración de autoescalado (como Kubernetes) que gestione instancias caídas, servidores bloqueados y picos de tráfico no mitigará completamente el error, pero puede reducir su impacto. Si utilizas el autoescalado o el reinicio automático, tu servidor de aplicaciones puede «sobrevivir» a la solicitud DoS del atacante, a menos que lo intente de nuevo o lo haga en todas las instancias de tu aplicación a la vez.
¿Y ahora qué? Cómo mitigar las cuatro CVE de React2Shell
Fastly sigue observando un volumen elevado y sostenido de actividad de React2Shell y esperamos que los atacantes también experimenten pronto con estas dos nuevas vulnerabilidades CVE. Aunque seguiremos compartiendo toda la información posible, es importante tener en cuenta que cualquier organización con aplicaciones vulnerables, independientemente del sector o la región, debe asumir que los atacantes ya las están sondeando como mínimo y que probablemente estén intentando explotarlas.
¿Cuáles deberían ser tus próximos pasos?
La máxima prioridad para las organizaciones sigue siendo evaluar la exposición y actualizar a versiones parcheadas de React y Next.js. Si bien actualizar tus sistemas es la única forma fiable de mitigar las cuatro CVE relacionadas con React2Shell, las soluciones de WAF de última generación y Bot Management de Fastly ofrecen parches virtuales y mucho más para bloquear los ataques mientras evalúas la exposición y realizas las actualizaciones necesarias.
Nuestro equipo está listo para ayudarte en todo lo que podamos. Ponte en contacto con nosotros en CVE-alert@fastly.com y te proporcionaremos asistencia inmediata y protección mientras trabajas en la implementación de los parches.

