Summary
On Monday, July 18, 2016, security researchers published information on a vulnerability in the handling of the HTTP_PROXY environment variable by specific Common Gateway Interface (CGI) scripts. While this vulnerability does not affect Fastly, web servers used as origins may run a variety of scripts, some of which may be vulnerable. This Security Advisory provides guidance to customers on how they can protect origin servers from attacks.
Impact
Vulnerable CGI scripts may expose outbound HTTP requests from a customer’s origin server to a Man-in-the-Middle attack. This type of attack may, depending on the script and its function, expose a website to disclose sensitive information.
Fix / Workarounds
On Monday, July 18, several third-party vendors released security updates to address this vulnerability. As a way to mitigate this vulnerability while updates are being tested and deployed, Fastly customers can remove the Proxy header at the CDN level. This will shield origin servers from exploitation.
Fastly customers can remove the Proxy header from inbound requests by adding the following Header object to their configuration:
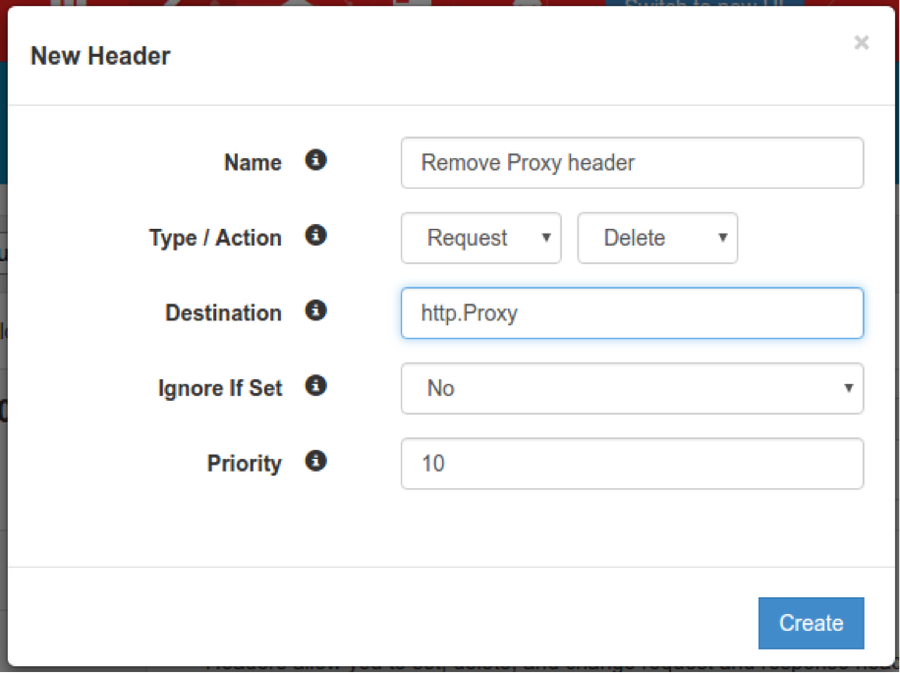
For more information on how to add Header objects, please refer to https://docs.fastly.com/en/guides/adding-or-modifying-headers-on-http-requests-and-responses.
Alternatively, Fastly customers can remove the Proxy header from inbound requests using custom VCL by adding the following line to the vcl_recvsub:
unset req.http.Proxy;Note that in some less common implementations, additional headers that begin with Proxy,such as Proxy_Host, Proxy_Port, Proxy_Password, Proxy_User, Proxy_Pass,and so on, may also be mishandled. These headers can also be removed by Fastly using either method described above.
Detail
A namespace conflict was identified by security researchers between the HTTP_PROXY environment variable and the Proxy: header as being parsed by the Common Gateway Interface (CGI) implementation. This namespace conflict allows an attacker to remotely configure the HTTP_PROXY environment variable on a web server by submitting a malicious Proxy: HTTP header.
This may cause a web server using an HTTP client which trusts the HTTP_PROXY environment variable to use a maliciously configured intermediate for outbound web requests, exposing potentially sensitive data.
While this vulnerability does not affect Fastly, web servers used as origins may run a variety of scripts, some of which may be vulnerable. Fastly customers can mitigate this vulnerability by filtering the HTTP Proxy: header at the CDN level through VCL.
More information
You can learn more about this vulnerability and find a list of CVE identifiers here.
