Throughout the end of 2021 and into early 2022 we’ve seen a resurgence of known remote code execution (RCE) vulnerabilities such as Log4Shell and SpringShell, resulting in data theft, compromised applications, and high remediation costs. Organizations are caught between a rock and a hard place as they have to simultaneously stop the immediate threat while actually fixing the vulnerable systems. Even when enterprises aren’t directly vulnerable to these specific attacks, their mere existence raises security posture questions.
These high-impact Common Vulnerability and Exposures (CVEs) are just examples of the insecurities found in web applications. While our recommendation is to remove or resolve the core of the issue through applying available patches, we also know real-world business conditions are not always conducive to patching software in a timely manner. From bureaucratic red tape to chained dependencies patching servers has been a pain in the side of the industry for years. This is why virtual patching was introduced.
What is virtual patching?
A virtual patch prevents the exploitation of a known vulnerability in an upstream system, generally in front of the vulnerable web application. Virtual patches defined in a WAF will intercept attacks in transit so malicious traffic never reaches your web application. This buys time in your development or DevSecOps processes to fix the underlying vulnerability while the patch is protecting your application at runtime. The patch is called virtual because your back-end applications and APIs still need to be updated and remediated but you can continue running your business until a proper fix can be put in place.
Virtual patching made easy
The Fastly Next-Gen WAF (powered by Signal Sciences) enables you to quickly and easily apply virtual patches that address various CVEs and immediately block requests seeking to leverage a CVE exploit.
We have two ways we do this:
The first is through SmartParse. A key benefit of our Next-Gen WAF's SmartParse technology is that it does not rely on traditional signatures to detect malicious or anomalous web requests. The lexical analysis SmartParse performs on each request results in a much lower false positive rate and is also more robust over time, since attacker techniques are more stable and predictable than application- or language-specific signatures.
As an example of this power, in early October 2021, a CVSS 7.5 vulnerability in the Apache HTTP server was publicly released. This bug required no rules to be created or any modifications at all in our next-gen WAF due to its parsing of commands and detection of the malicious behavior in the default configuration. SmartParse is a core technical capability of our WAF that’s automatically provided to all customers.
The second way to virtually patch using our next-gen WAF is through templated rules. Within the console, you can select and enable templated rules that cover various CVEs. In order to provide our customers the broadest possible protection we’ve recently made CVE capabilities available to all plans, including Essential plan customers.
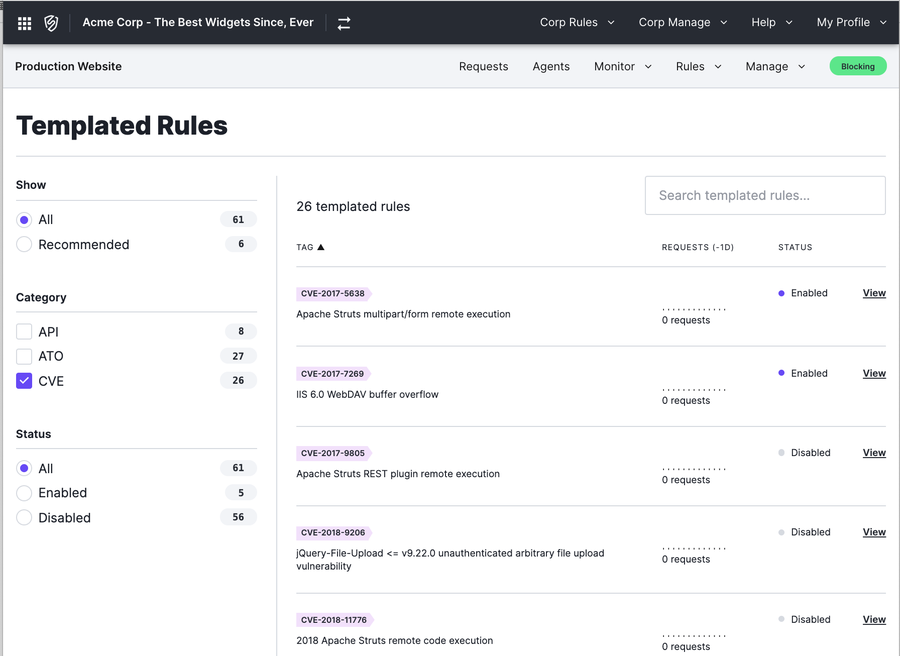
Between SmartParse’s built-in detection capability and those provided through templated rules, we can readily provide multiple layers of defense for our customers.
Fastly Next-Gen WAF customers can stay informed of new CVE rules by subscribing to virtual patch announcements in your account settings. Not yet a next-gen WAF customer? Reach out to us and we’ll show you how to get simple, yet performant and effective web application and API security.
