Distributed denial of service (DDoS) attacks are a pretty nasty topic; as CEO Artur Bergman notes, it’s emotionally damaging to be a victim of a DDoS. Fundamentally, a DDoS is an attempt to make machine or network resources unavailable to the intended users: an attack on your infrastructure, customers, and employees — on the entire being of your company. As an edge cloud platform with a large network of globally distributed points of presence (POPs), we’re in a unique position to track global traffic patterns, and we defend our customers against attacks on a daily basis. In this post, we’ll take a look back at the history of DDoS, sharing how these attacks have evolved and the trends we’re seeing. Getting a handle on the various shapes and sizes of DDoS will help inform how you address these attacks on your own infrastructure — you may not always be able to predict attacks, but knowing what’s out there and preparing for the worst will help you protect and mitigate.
In the last 20 years, DDoS attacks have become front-page news; they’re often tied to high-profile events — everything from the Olympics and Super Bowl to political events such as elections, political parties, and news coverage are targeted. DDoS attacks are an easy, accessible way for people to achieve their aims — whether that’s putting a competitor out of business or silencing somebody. It’s all about making a statement in a very visible, impactful way.
For context, here’s what normal traffic looks like:
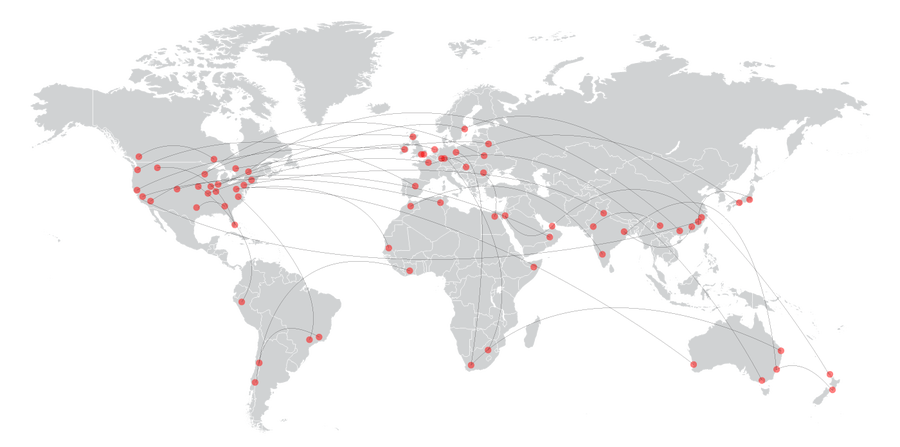
Here’s a DDoS attack – you have traffic coming from a lot of different sources and going where it shouldn’t:
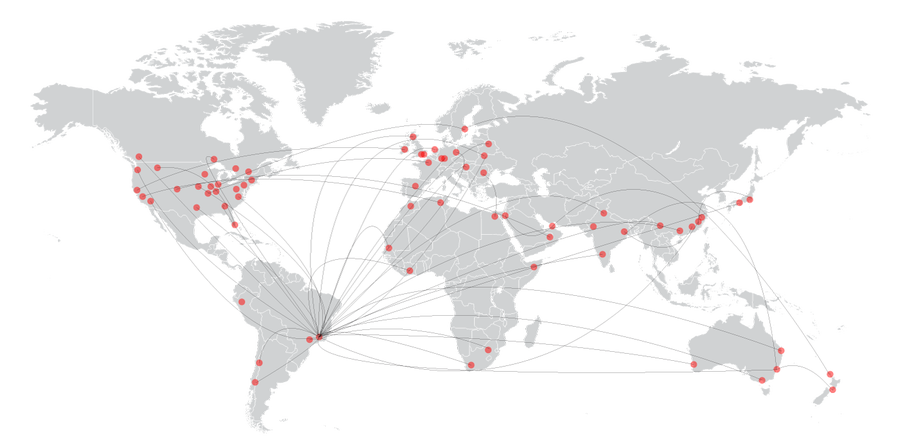
Here’s another view — a medium-sized DDoS, at about 160 Gbps:
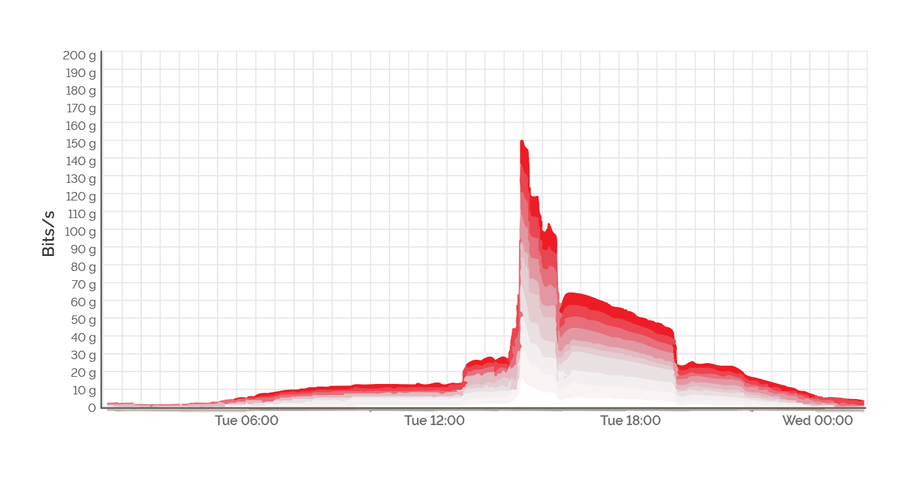
You can see the DDoS begin probing about two hours before the full attack, and then the floodgates open.
DDoSes can be divided into types:
Economically rational attacks, during which you get the ransom letter, lately using bitcoin. These are actually the easiest to deal with because all you need to do is make it more expensive for the attacker to attack you than the expected gain from the ransom.
Hate-based or ideologically motivated. The worst attacks are economically irrational. These attackers fall into two categories:
Individual(s) without much budget; they might hate you, or they might hate one of your customers, or they might hate the city of New York and randomly pick a site that has the name New York in it.
A nation state with political or ideological motivations, such as the 2007 Russian cyberattacks on Estonia.
Retribution/punitive attacks, like personal attacks in gaming or industry attacks like those against the US financial industry starting in 2012.
Distractions, like the January 2016 attacks on Sony Playstation Network, which were claimed by hacking group Phantom Squad but with no “overt financial or political motive.”
Competitive advantage, or service disruption attacks, which serve to tarnish a competitor’s reputation by making them unavailable to users.
DDoS: an ever-evolving landscape
The rise in popularity of Internet of Things (IoT) devices — like DVRs, IP cameras, and NVRs (network video recorders) — has set the stage for massive IoT botnet attacks. The largest and perhaps most famous of these were last year’s Mirai attacks against security journalist Brian Krebs and DNS provider Dyn. The connections poorly secured IoT devices have to big networks plus an uptick in bitcoin-enabled extortion provide ample and easy opportunities for attackers. For this reason a number of people in the industry have been keeping and eye on the new IOT Reaper (aka IOTROOP) botnet, which has yet to launch any DDoS attacks of note.
The nature and complexity of DDoS attacks can vary, however — i.e., in terms of whether you’re being attacked at the application layer, in the kernel, or the network, and whether you’re being attacked directly or indirectly. Attacks can change as they’re happening as attackers try to evade defenses.
Here’s how varied and complex DDoS attacks can be (adapted from a 2004 paper by J Mirkovic and P Reiher):
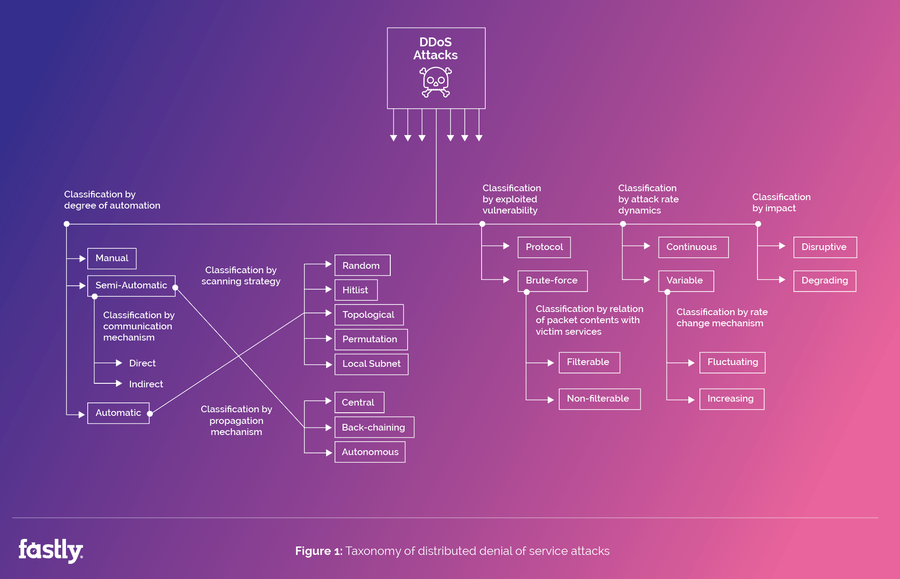
How did we get here? Here’s a look back at DDoS attack traffic evolution:
In the late 90s, attacks were relatively unsophisticated, taking advantage of simply misconfigured networks to exhaust their target’s CPU by overwhelming servers with inbound requests — i.e., SYN flood, ICMP (Smurf) floods, etc. Attacks like Teardrop were designed to exploit kernel bugs, causing kernels to crash. This was also the time of Tribe Flood Networks, actors like Mixter in Israel and Mafiaboy in Montreal, and the CNN / Yahoo attacks.
As early attack methods and vulnerabilities were patched, attacks in the early 2000s went straight for bandwidth consumption. Prototype malware such as the worms Code Red and Nimda aimed to fill the pipes, overwhelming origin servers with requests. These methods led to the first mitigation services and devices designed to protect businesses.
The late 2000s brought TCP state machine issues, such as state holding, in which you keep a TCP connection in an unproductive state, exhausting kernel resources without doing anything useful, eating away at new connection slots. Defensive mechanisms became much more sophisticated — you could, for example, use TCP state machines to lock up your adversary’s TCP state machines. Further, as the world began to converge on using everything over HTTP or HTTPS, network service layer filtering became impossible and introduced the requirements of wire-speed packet inspection.
By early 2010, what’s old is new again: web application bugs (e.g., RefRef with SQL injection to lock up the backend, preventing the front end from talking to the database), DNS query floods, GET floods, UDP amplification, and cache busting attacks that employ random payloads to thwart application caches and increase the workload on the backend servers.
Throughout this time, the theme has remained the same: the attacker wishes to overwhelm the victim’s resources, and malware or exploits provided leverage. The victim must expend time and effort to drop attack traffic and maintain legitimate traffic. Each side must expect different amounts of work to achieve their aims, with the defender typically paying more money than the attacker.
Stay tuned — in our next post, we’ll share some of the methods we use to protect our customers from DDoS attacks, including leveraging both the Security Research and Network Engineering teams. We’ll offer an inside look at a DDoS attack, plus how you can apply the lessons we’ve learned to your own infrastructure.

