Looking at recent headlines of the latest malware, ransomware, or “encryption event,” it’s clear that a defense-in-depth strategy is key to ensuring you never have a single point of failure across your network architecture.
One key capability for protecting your application layer is the ability to verify the reputation of a file, image, or other content against an API. Many people still believe the best practice for this is to have a local sandbox for malware scanning, such as Cuckoo automated malware analysis. This requires domain-specific knowledge to interpret the malware scan results.
What if you could do that at the network edge, ensuring that a malicious request never even reaches your origin? And what if you could do it on a platform that allows you to use a crowd-sourced interpretation of the malware scan results without requiring the need to perform local file scanning?
Fastly’s Next-Gen WAF (NGWAF) protects your applications and APIs wherever they live, and building on Fastly means you have a reliable infrastructure that ensures your site’s performance and availability. Our ability to validate malware at the edge combines our best-in-class security and delivery products and allows us to make better blocking decisions while reducing origin load and costs. If you want to prevent malicious files from ever touching your infrastructure, let’s walk through the benefits of NGWAF edge deployment and a few examples.
Malware protection at the edge
Edge computing, which allows devices to process data requests closer to the network’s edge, is rapidly transforming how businesses operate and enables them to deliver exceptional end-user experiences. For example, a concert ticketing website can deliver waiting room tokens for popular events, or an airline site can pre-load user seat and meal preferences based on customer data. When this information is stored and delivered at the network edge, it makes customers happy, saves on origin costs, and helps businesses maintain their competitive edge.
Not only is the edge valuable for customer-facing experiences, but for threat mitigation as well. Ransomware attacks are continuing to rise, and we can see the fallout of these attacks, especially among healthcare and government entities. According to Malwarebytes, “In February, the most widely used ransomware-as-a-service (RaaS) posted a total of 126 victims on its leak site—a record high since we started tracking the leaks in February 2022.”
Ransomware’s effectiveness is due in part to how easily it can slip through the cracks. Just one click on an infected file or link can lock down an entire organization. A defense-in-depth approach, like frequent software patching and endpoint protection, is the gold standard for most threat mitigation. But scanning and verifying malware at the edge can take your security strategy to the next level.
Application benefits at the edge
Businesses are choosing to move their applications to the edge because they can immediately see the impact of managing application traffic away from their origin. The NGWAF at the edge provides a performant layer of defense while delivering on:
Speed: Scans requests for malware or other malicious payloads at faster speeds than at origin, keeping potentially-exposed API endpoints better protected.
Scope: Allows customers to utilize crowd-sourced, reputation-based scores and several scanning engines, to get a more holistic view of the request’s validity.
Savings: Utilizes Fastly’s global POP infrastructure to reduce latency and save on origin costs by stopping invalid requests from executing.
How it works on the Fastly edge
Fastly can help you check file upload content against the reputation-based API of your choosing. This Fiddle example demonstrates the hashing of the POST Body, then verifying the hash against the VirusTotal API.
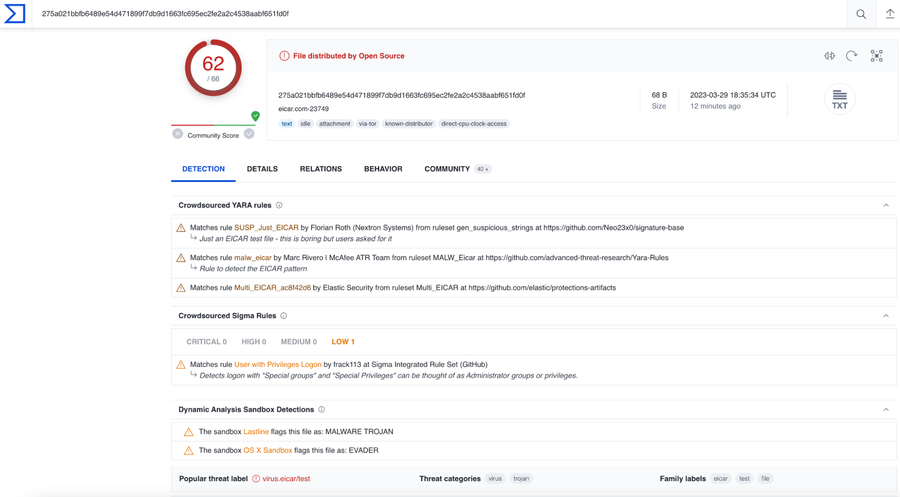
You can see in the example above the “virus-scan-result:” Request header has been added, which contains the Virus Total reputation and malicious score.
With the C@E Javascript SDK, you can develop complex logic using the Javascript language your team already knows. This allows you to develop custom security conditions and manage the actions taken on the Request before forwarding it to your backend applications.
You can easily define content inspection based on the Request Path “/upload” application-content type “application/pdf”, or other attributes. Review our JS Compute documentation for more information on the Request Object.
Using this data enrichment at the edge, you can take more informed actions on what content can reach your applications.
Fastly is continuing to look at how we enable our customers to secure their web applications by pushing content delivery to the edge. Using our JS Compute framework, you can defend your application from the increasing threat of malware and ransomware. Stay ahead of the attackers by pushing the security perimeter to the edge.
The possibilities with serverless edge computing are not limited to security; explore our other use cases.
Contact us if you or your web application security team want to learn more about Fastly Compute, JS Compute, or the Next-Gen WAF. Our professional services team can actively work with you to improve your security posture.

