A Distributed Denial of Service (DDoS) is a form of cyberattack where an attacker uses numerous compromised computers (called a botnet) to produce a volumetric attack, with the goal of overwhelming a target system. This type of attack can render the target (a service or server) unavailable to legitimate users. You can think of a DDoS attack as a flood of illegitimate traffic from various sources that effectively incapacitates the target system.
How is a DDoS attack related to a DoS attack?
A DDoS attack is a type of DoS attack. Their key difference is that a DoS attack stems from a single source/ IP address, while a DDoS attack, as its name implies, is distributed: it originates from numerous sources / IP addresses. A DDoS attack, by using numerous compromised devices, can intensify the attack and make it harder for the target to recover and defend against the attack.
What are the different types of DDoS attacks?
You can group DDoS attacks based on the targeted Open Systems Interconnection (OSI) layer. Most common attacks happen at the Network (OSI layer 3), Transport (OSI layer 4), and Application (OSI layer 7) layers. Few of the many cyberattacks today are more overwhelming and devastating than DDoS attacks. These malicious attacks can come at any time and take targeted websites offline, leading to massive service interruptions and substantial financial losses.
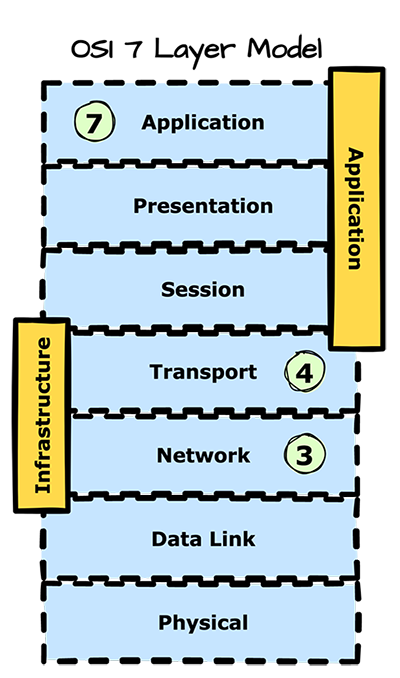
What is a layer 3/4 DDoS attack?
Layers 3 and 4 are the infrastructure layer. Common DDoS attack vectors at these layers include SYN floods, UDP floods, and Internet Control Message Protocol (ICMP)
attacks. Layer 3 is the network layer responsible for deciding which physical path data should move through the network. Layer 4 provides data transfer between hosts and ensures data integrity and completeness of transfer performed by the Transport Control Protocol (TCP).
Attacks targeting these two layers generate massive traffic volume and aim to overload the network's available capacity or group of hosts. The good news is these styles of attacks have clear signatures and are easier to detect and mitigate.
What is a layer 7 DDoS attack?
Layer 7 is the application layer. These attacks tend to be less common, while also being more sophisticated. From a volume standpoint, these attacks are less about a sudden influx of traffic than infrastructure layer attacks. Still, they target critical vital parts of the application, negatively impacting the performance of the target. A real-world example of this attack is to flood an application login page or target an exposed API with an expensive search request, resulting in a degraded experience for the end users. Reactive remediation of these attacks is costly. Small to medium-sized businesses (SMBs) spend an average of $120,000 restoring service and managing operations during a DDoS attack.
What risks do DDoS attacks pose to a business?
The consequences of DDoS go far beyond just a temporary outage. Here is how these attacks can affect your business. They can:
Lead to Financial Losses: Every minute of downtime means lost earnings from customers who cannot purchase products or access services on your site. Prolonged or repeated attacks add to massive costs that damage your bottom line.
Hinder Normal Business Operations: Operational delays, canceled orders, and stalled projects harm productivity and satisfaction. When certain services are unavailable during an attack, it becomes challenging to run your business.
Cause Reputational Damage: Customers today expect consistent and reliable digital experiences from companies. A DDoS attack drawing out website downtime reflects poorly on your brand in the eyes of these clients. It may cause them to lose trust in your business and switch to competitors.
Increase Security Risks: When attacks overwhelm your existing security, it exposes vulnerabilities that hackers can exploit further. This elevates risks of data theft or network infiltration even after the DDoS ends. Sensitive customer data may get stolen due to security gaps attacks help uncover, deepening the damage.
How can you protect your applications from DDoS attacks?
Understand traffic patterns: The first line of defense is to create a traffic profile. This profile includes what “good” traffic looks like and sets expectations for expected traffic volumes across your network. Monitoring your traffic through this profile allows you to configure rules to accept as much traffic as your infrastructure can handle without impacting your end users.
Use rate limiting: Rate limiting provides a baseline, and you can then put advanced detection methods in place to receive traffic that has been validated by analyzing additional variables. It takes one minor security blip to cause irreparable harm to your network and servers and send your employees through the five emotional stages of a DDoS attack. So do your diligence from the onset.
Minimize exposure: One of the easiest ways to mitigate DDoS attacks is to shrink the surface area that can be attacked, ultimately reducing the options for attackers and enabling you to architect countermeasures and protections in one place. You should ensure that you are not exposing your applications and hosts to ports, protocols, and other applications from which you do not expect communication. In most cases, you can achieve this by placing your infrastructure resources behind a proxy Content Delivery Network (CDN), which restricts direct internet traffic to certain parts of your infrastructure. In other cases, you can use a firewall or Access Control Lists (ACLS) to control traffic reaching specific applications.
Deploy an application-based firewall: If your application has internet access, you get attacked multiple times daily. On average, an application with internet connectivity gets attacked every 39 seconds. A good practice is to use a Web Application Firewall (WAF) against attacks. A good starting point is to mitigate OWASP Top 10 type attacks actively, and then you should be able to create a customized traffic profile against additional invalid requests. For example, these requests may be masquerading as legitimate traffic from known malicious IPs or from a geographic part of the world in which you don’t do business. A WAF is also helpful in mitigating attacks as you can leverage experienced support to study the traffic heuristics and create custom-tailored protection for your application.
Scale by design: While not the best solution in isolation, increasing your bandwidth (transit) capacity or server (computational) capacity to absorb and mitigate attacks may be an option. When designing and building your applications, make sure you have redundant connectivity to the internet that allows you to handle spikes in traffic. A common practice is to use load balancing to continually monitor and shift loads between available resources to prevent overloading any one point. Additionally, you can create your web applications with a CDN in mind, providing an additional layer of network infrastructure for serving content often closer to your end-users. Most DDoS attacks are volumetric and consume massive amounts of resources, and your application must scale up or down quickly on computation. The distributed nature of a CDN essentially spreads out the attack to the point that it becomes easily absorbed. CDNs also unlock additional methods to thwart the most sophisticated attacks. Developing an attack profile allows CDNs to remove or slow down malicious traffic.
You can read more about how to mitigate a DDoS attack with our DDoS best practices guidelines.
How can you stop a DDoS attack?
Defending against DDoS attacks requires a multi-pronged approach combining proactive measures and reactive strategies. While completely preventing DDoS attacks may be challenging, organizations can significantly mitigate their impact by implementing a solid defense plan. Let’s look at the key steps and best practices to help protect your digital assets and maintain business continuity in the face of potential DDoS threats.
Monitor Traffic Patterns
Your first line of defense is constant monitoring. Install tools to analyze website traffic 24/7 and alert you to unusual spikes or changes. By spotting anomalies early, your team can investigate and stop bots or potential attacks before serious overload occurs.
Use a Web Application Firewall (WAF)
Fastly’s Next-Gen WAF sits in front of your web servers, filtering requests for signs of malicious activity. It can stop bots and detect and block common exploits like SQL injection or cross-site scripting before they reach your applications. By preventing harmful traffic, Fastly’s WAF protects you from dealing with disruptions after the fact.
Implement Rate Limiting
No system can handle unlimited traffic indefinitely. Set access thresholds using
edge rate limiting, so abnormal volumes are automatically managed without impacting normal users. This ensures your digital presence remains responsive for genuine customers during episodes of elevated traffic loads.
Use Content Delivery Networks (CDNs)
CDNs make your website’s digital assets available from multiple server locations worldwide. This distributed architecture means that if one region faces elevated traffic, others nearby can handle the extra load to ensure you can continue serving customers.
Employ IP Blacklisting
You also have the option of banning specific IP addresses known to cause problems in the past. Keep records of addresses engaged in questionable traffic patterns and automatically reject their future requests. This denies bad actors the ability to disrupt your business's operations.
Conduct Regular Security Audits
Review your defenses periodically. As threats evolve, so too must protections. By scheduling security audits, your business can ensure tools remain up-to-date and appropriately configured to safeguard operations.
Establish an Incident Response Plan
Even the most robust measures may not prevent every attack. Have a detailed plan prepared if issues arise, so your team can respond rapidly and minimize any impact. With a process ready to execute, you can address disruptions efficiently and continue serving customers.
To learn more about integrated DDoS protections, check out this resource on
why security teams are switching to Fastly's next-gen WAF
Why Fastly Is Your Best Solution to Preventing DDoS Attacks
Maintaining comprehensive security against DDoS attacks presents major challenges in terms of cost, complexity, false positives, evolving threats, and resource intensity. However, Fastly's cloud-based DDoS protection solution directly resolves each of these concerns.
The key benefits of Fastly’s DDoS Protection include the following:
Lowers Costs: Fastly offers cost-effective DDoS protection, which is included with its CDN services. Flexible payment options let you choose the package suited to your needs, with unlimited overage protection. Consolidating with a single vendor for security, CDN, and edge cloud services is the more affordable choice.
Simplifies Complexity: Fastly's solution requires no complex setup or manual tuning on your side. The network automatically absorbs layer 3/4 attacks, while the next-gen WAF seamlessly handles Layer 7 threats.
Reduces False Positives: Fastly's advanced SmartParse detection engine accurately classifies requests while minimizing the false positives that could block real users.
Continuously Evolves: Fastly enhances detection and mitigation based on solid intelligence, letting you stay ahead of evolving global attack trends, such as the recent Reset attacks.
Resource Efficient: Fastly's massive 336 Tbsp network has a built-in capacity to absorb even extraordinary attacks without performance impacts. Automated edge mitigation also reduces the origin load.
Sign up for a free trial to learn more about how Fastly can bring you peace of mind and stop bad actors from interfering with your digital presence