About the architecture
The Next-Gen WAF is an application security monitoring system that proactively monitors and protects your web application from malicious traffic. It uses the following core architectural components:
- Next-Gen WAF module (optional): the component responsible for handling requests to, or on, your web application. Your deployment method determines whether the Next-Gen WAF uses this optional component.
- Next-Gen WAF agent: the component responsible for processing requests and communicating with our cloud engine. If your deployment does not use the optional module component, the agent also performs the role of the module.
- cloud engine: the component responsible for sending data between the Next-Gen WAF agent and other sources.
Data flow within the Next-Gen WAF
- Deployment with module
- Deployment without module
This diagram illustrates the data flow within the Next-Gen WAF when it uses the module component. The module intercepts incoming requests and queries the agent. The agent then applies security rules to these requests and transmits its decisions back to the module. Furthermore, the agent maintains bidirectional communication with the cloud engine, receiving updated configurations and uploading redacted request data. The cloud engine, in turn, forwards this data to various output destinations, including the control panel and API you use to interact with the Next-Gen WAF, as well as any configured integrations (also known as alerts).
About the module
The Next-Gen WAF module is an optional architecture component that is responsible for handling requests to, or on, your web application. It listens for incoming requests and passes them to the Next-Gen WAF agent for a decision. After receiving a decision from the agent, the module handles requests in accordance with that decision (e.g, block requests).
Your deployment method determines whether the Next-Gen WAF uses this optional component. The agent performs the module's role if your deployment doesn't use the module component.
| Deployment method | Uses the module | Module variation |
|---|---|---|
| Cloud WAF | ❌ | Not applicable |
| Edge WAF | ✅ | Your Fastly CDN or compute service functions as the module. |
| Module-agent | ✅ | The module can exist as a plugin to your web server (e.g., NGINX and Apache) or be deployed at the application layer (e.g., .Net Core and Node.js). |
| Platform as a Service (PaaS) | ❌ | Not applicable |
| Reverse proxy | ❌ | Not applicable |
About the agent
- Deployment with module
- Deployment without module
For deployments that use the Next-Gen WAF module, the Next-Gen WAF agent (formerly known as the Signal Sciences agent) is responsible for processing requests and communicating with our cloud engine. After receiving a request from the module, the agent:
- uses your active rules and threshold configurations to determine how the request should be handled (e.g., allow or block).
- tags requests with the appropriate signals.
- redacts sensitive information from the request.
- relays the request and its decision back to the module.
The agent also communicates asynchronously with our cloud engine every 30 seconds. It downloads new and updated configurations from the cloud engine and uploads redacted request and response data to the cloud engine per our data storage policy.
If the agent experiences issues or unavailability, your web application will continue to function because the module fails open if it doesn’t hear back from the agent within a set time limit. Additionally, if the agent loses the ability to communicate with the cloud engine, the agent will continue to function with a few caveats.
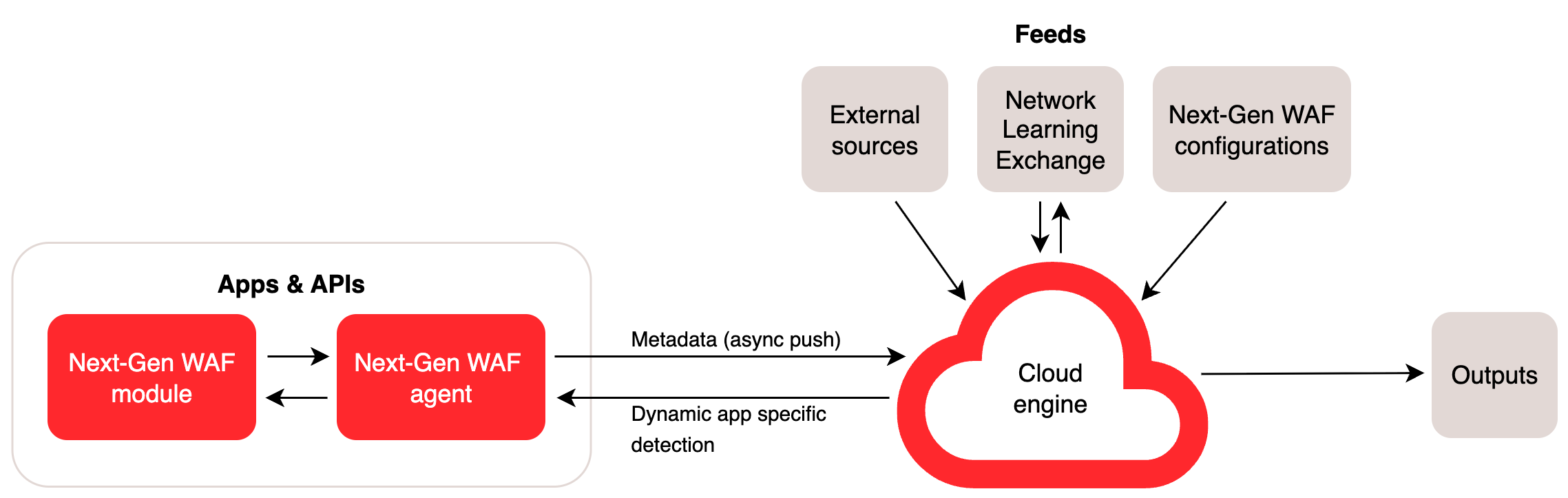
About the cloud engine
The cloud engine is the architecture component that serves as the control plane between the Next-Gen WAF agent and other sources. Specifically, the cloud engine:
- forwards corp (also known as account) and site (workspace) configurations (e.g., rules and lists) to your Next-Gen WAF agent. The agent uses this information to determine how to handle requests.
- forwards anomalous request and response data and performance metrics from the Next-Gen WAF agent to the control panel you have access to and any third-party integrations that you have set up.
- forwards attack data from the Next-Gen WAF agent to our Network Learning Exchange (NLX). The NLX is an IP address reputation feed that aggregates and analyzes attack data from our subscriber network to identify potential bad actors.
- forwards the list of potential bad actors from the NLX to your Next-Gen WAF agent. Your agent tags requests that are from the identified IP addresses and that contain at least one signal with the SigSci Malicious IPs (
SIGSCI-IP) anomaly signal. - forwards information from external sources to the Next-Gen WAF agent. For example, the cloud engine imports the list of IP addresses that have engaged in malicious activity from SANS Internet Storm Center and sends them to the agent. The agent then tags requests that are from the identified IP address list with the Malicious IP Traffic (
SANS) anomaly signal.
We host the cloud engine in AWS West across multiple availability zones.
Deploying the WAF alongside a CDN
If you already have a Fastly service, you can deploy the Next-Gen WAF alongside your Fastly service via the Edge WAF deployment method. With this method, your deployment will be hosted on Fastly’s Edge Cloud platform via our global network of POPs.
If you'd like to use another CDN provider, you can use a header (e.g., X-Forwarded-For) to obtain the true client IP address. For more information, check out our Client IP addresses guide.