Blocking requests with invalid challenge tokens
After successfully completing a client challenge, the client receives a token stored as a browser cookie. To validate this token on subsequent requests and block requests with invalid tokens, create two request rules.
| Request rule | Action types | Description |
|---|---|---|
| 1 | Verify token | Check if the web client solved a challenge on a previous request. This rule will add either the CHALLENGE-TOKEN-VALID or CHALLENGE-TOKEN-INVALID signal to the request. |
| 2 | Block (Optional) Add signal | Block requests tagged with the CHALLENGE-TOKEN-INVALID signal. If you have multiple rules that block requests with invalid challenge tokens, you can also optionally add a custom signal to matching requests for easier rule monitoring. |
HINT: In most cases, these rules only need to target POST requests. This is because the browser challenge is typically issued on GET requests and the client cannot proceed until they successfully solve a challenge.
Prerequisites
Before creating rules to handle requests from clients that failed a challenge, you must:
- enable client challenges on the service where you intend to use them.
- add a client challenge by creating a rule or modifying the HTML of the page where you'd like the challenge to be sent.
Protecting a POST endpoint example
Let's say that you want to protect a POST endpoint, in this case www.example.com/login, and that you've already added a challenge for the endpoint. To protect the endpoint, you need to configure two request rules that will:
- verify the token on POST requests to
www.example.com/login, and - block requests tagged with the
CHALLENGE-TOKEN-INVALIDsignal.
IMPORTANT: Be aware that this example uses values (e.g., hostnames and paths) that may not be the same as those used by your particular web application.
Adding the verify token rule
The first request rule verifies the token on POST requests to www.example.com/login.
- Next-Gen WAF control panel
- Fastly control panel
- Log in to the Next-Gen WAF control panel.
- From the Sites menu, select a site if you have more than one site.
From the Rules menu, select Site Rules.
Click Add site rule.
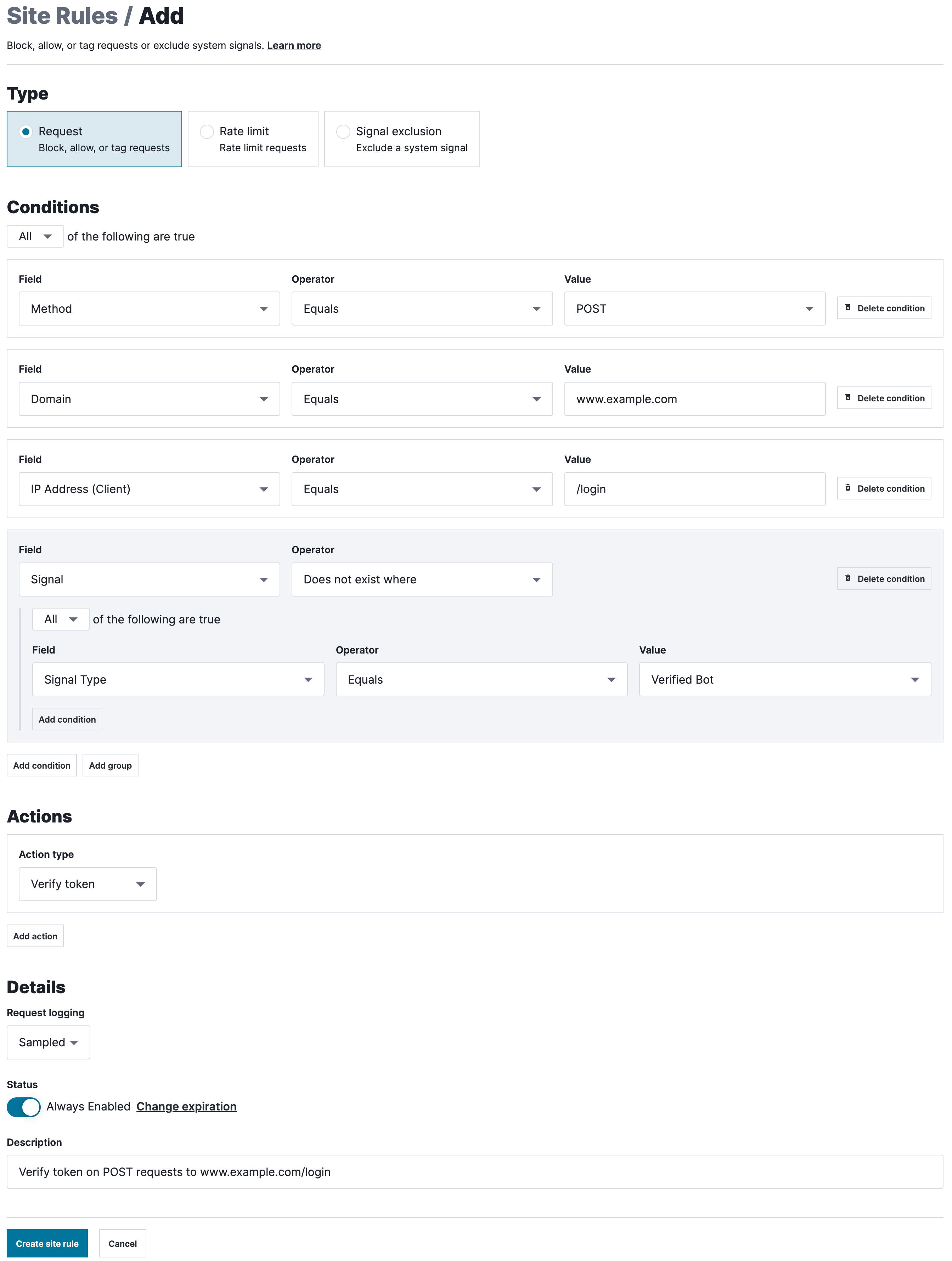
Add the following three conditions to ensure the WAF only applies this rule to HTTP POST requests where the domain is
www.example.comand the request path is/login.Condition Field Operator Value 1 Method Equals POST 2 Domain Equals www.example.com3 Path Equals /loginAdd the following condition to ensure the WAF does not apply this rule to requests made by verified bots.
- From the first Field menu, select Signal.
- From the first Operator menu, select Does not exist where.
- From the second Field menu, select Signal Type.
- From the second Operator menu, select Equals.
- From the Value menu, select Verified Bot.
From the Action type menu, select Verify token to check whether the client has successfully solved a challenge on a previous request.
In the Description field, enter
Verify token on POST requests to www.example.com/login.Click Create site rule.
HINT: This rule only checks whether the client has successfully solved a challenge on a previous request. You must add a second rule for the WAF to block requests from clients that haven't successfully solved a challenge.
Adding the block rule
The second request rule blocks POST requests to www.example.com/login when there isn't a valid token. It also tags matching requests with the Login attempt with invalid token custom signal to make it easier to monitor the rule.
IMPORTANT: Before creating this rule, create a custom signal named Login attempt with invalid token.
- Next-Gen WAF control panel
- Fastly control panel
- Log in to the Next-Gen WAF control panel.
- From the Sites menu, select a site if you have more than one site.
From the Rules menu, select Site Rules.
Click Add site rule.
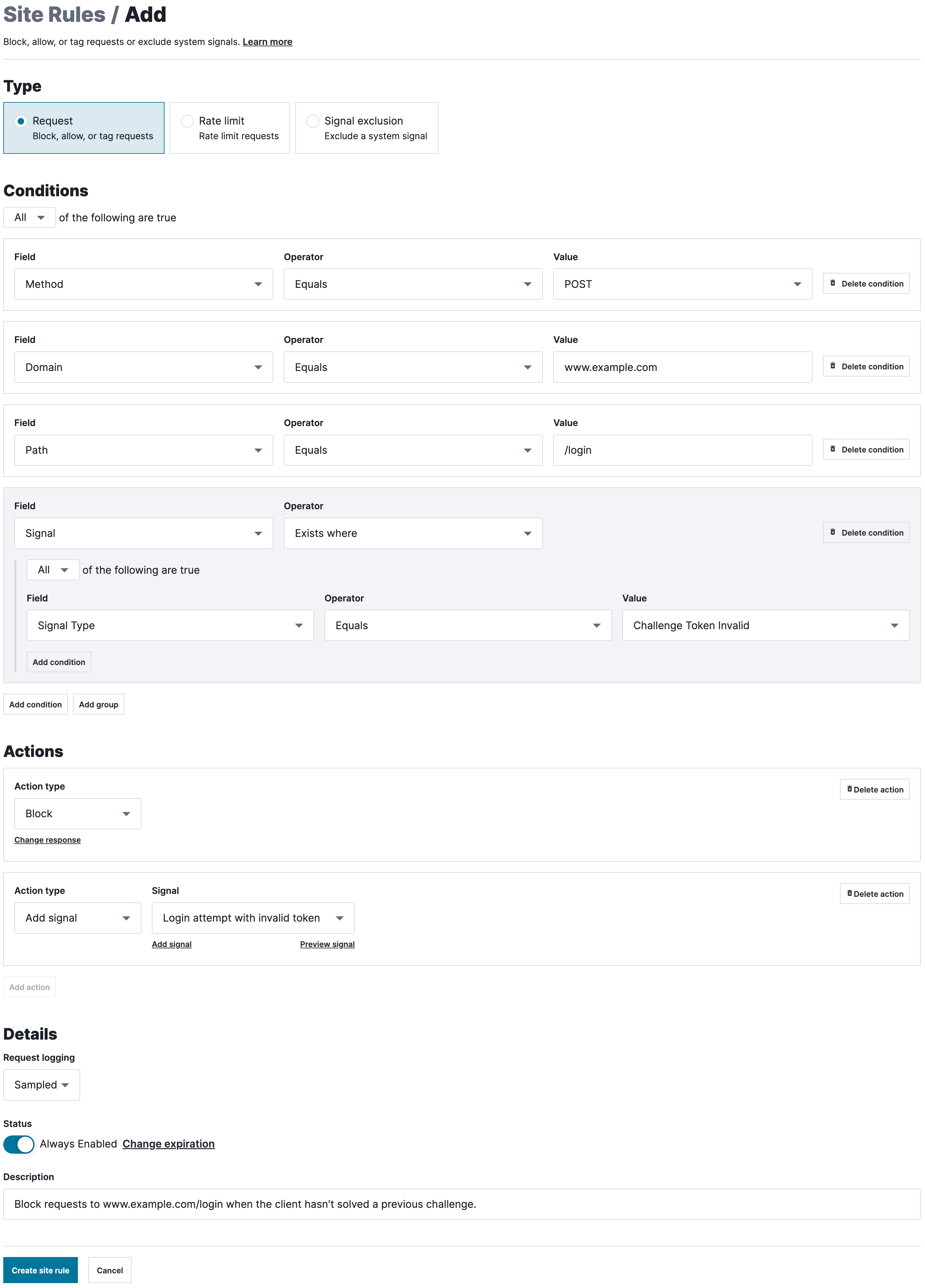
Add the following three conditions to ensure the WAF only applies this rule to HTTP POST requests where the domain is
www.example.comand the request path is/login.Condition Field Operator Value 1 Method Equals POST 2 Domain Equals www.example.com3 Path Equals /loginAdd the following conditions to ensure the WAF only applies this rule to requests tagged with the
CHALLENGE-TOKEN-INVALIDsignal.- From the first Field menu, select Signal.
- From the first Operator menu, select Exists where.
- From the second Field menu, select Signal Type.
- From the second Operator menu, select Equals.
- From the Value menu, select Challenge Token Invalid.
From the Action type menu, select Block.
Click Add action. New menus appear.
From the new Action type menu, select Add signal and from the Signal menu select the
Login attempt with invalid tokencustom signal.In the Description field, enter
Block requests to www.example.com/login when the client hasn't solved a previous challenge..Click Create site rule.