About reverse proxy deployment
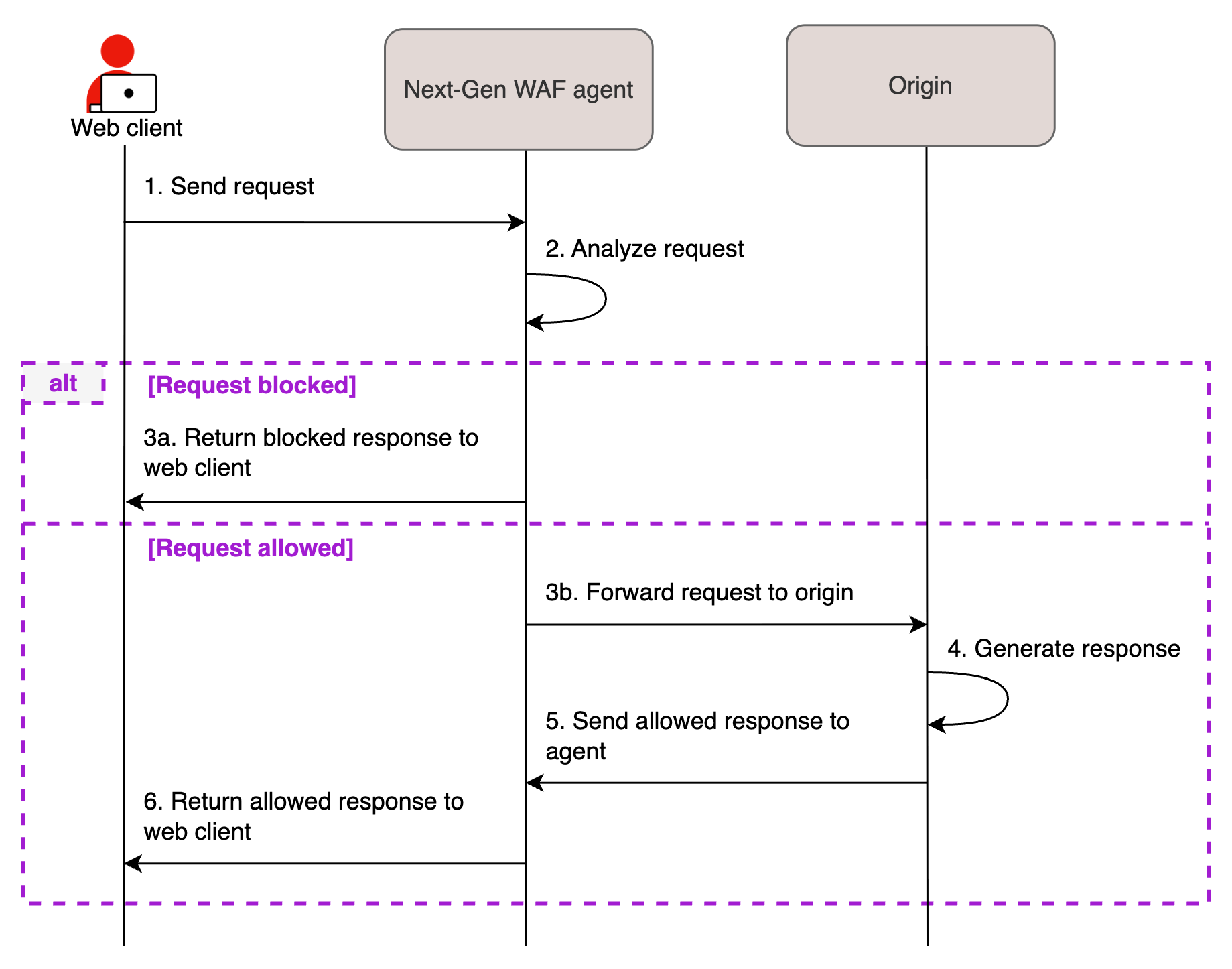
Deploying the Next-Gen WAF as a reverse proxy allows you to host the WAF directly on your local environment without having to make changes to your web server or code. Once deployed, the Next-Gen WAF agent is positioned between incoming traffic and your origin. The agent processes requests to your web application and communicates with our cloud engine. If the agent is down, all traffic is blocked (fail-close design).
HINT: Is a reverse proxy deployment not right for you? Check out our other deployment options.
Setting up reverse proxy deployments
To set up a reverse proxy deployment, complete the following steps:
- Determine the reverse proxy variation that you'd like to use to integrate the Next-Gen WAF into your request flow.
- Install the Next-Gen WAF agent by following the appropriate installation instructions for your operating system.
- Configure the agent to operate as a reverse proxy by following the appropriate guide for your selected reverse proxy variation.
After setting up your deployment, you can optionally:
- use attack tooling to verify that the Next-Gen WAF is monitoring your web application and identifying malicious and anomalous requests.
- enable the agent auto-update service. The agent auto-update service checks at regularly occurring intervals for a new version of the agent and updates the agent when a new version is available.
- set up agent alerts to inform you when the number of online agents reaches a specified threshold or the average number of requests per second (RPS) for all agents across all sites (workspaces) reaches a specified threshold.
Reverse proxy variations
The Next-Gen WAF supports the following reverse proxy variations.
Agent reverse proxy mode
The Next-Gen WAF agent can be configured to run as a reverse proxy. In reverse proxy mode, the agent interacts directly with requests and responses without the need for a module. Running the agent in reverse proxy mode is ideal when a module for your web service does not yet exist or you do not want to modify your web service configuration (e.g., while testing the product). In this mode, the agent sits inline as a service in front of your web service. For more information, check out our Configuring Agent reverse proxy deployments guide.
Envoy proxy integration
The Next-Gen WAF agent can integrate directly with Envoy, a cloud-native reverse proxy, to inspect and protect web traffic. For more information, check out our Configuring Envoy proxy deployments guide.
gRPC proxy deployments
The Next-Gen WAF agent can act as a proxy for gRPC traffic to allow inspection of protobuf-based gRPC messages (Content-Type: application/grpc). For more information, check out our Configuring gRPC proxy deployments guide.
Istio service mesh integration
The Next-Gen WAF agent can integrate with Istio service mesh to inspect and protect north-south and east-west traffic in microservices architecture applications. For more information, check out our guide on Istio and Kubernetes.
AWS Lambda integration
The Next-Gen WAF agent can integrate with AWS Lambda. To provide on-demand protection, the agent can be set up to initialize with each function and close out upon function completion. For more information, check out our guide on AWS Lambda.
Egress HTTP proxies
You can configure the Next-Gen WAF agent to use a proxy for egress traffic.